On Friday, a massive ransomware attack which initially focused on Russia spread to 74 countries worldwide. Cybersecurity firm Avast said that number may be as high as 99 countries, with more than 75,000 attacks. It said the majority of attacks targeted Russia, Ukraine and Taiwan.
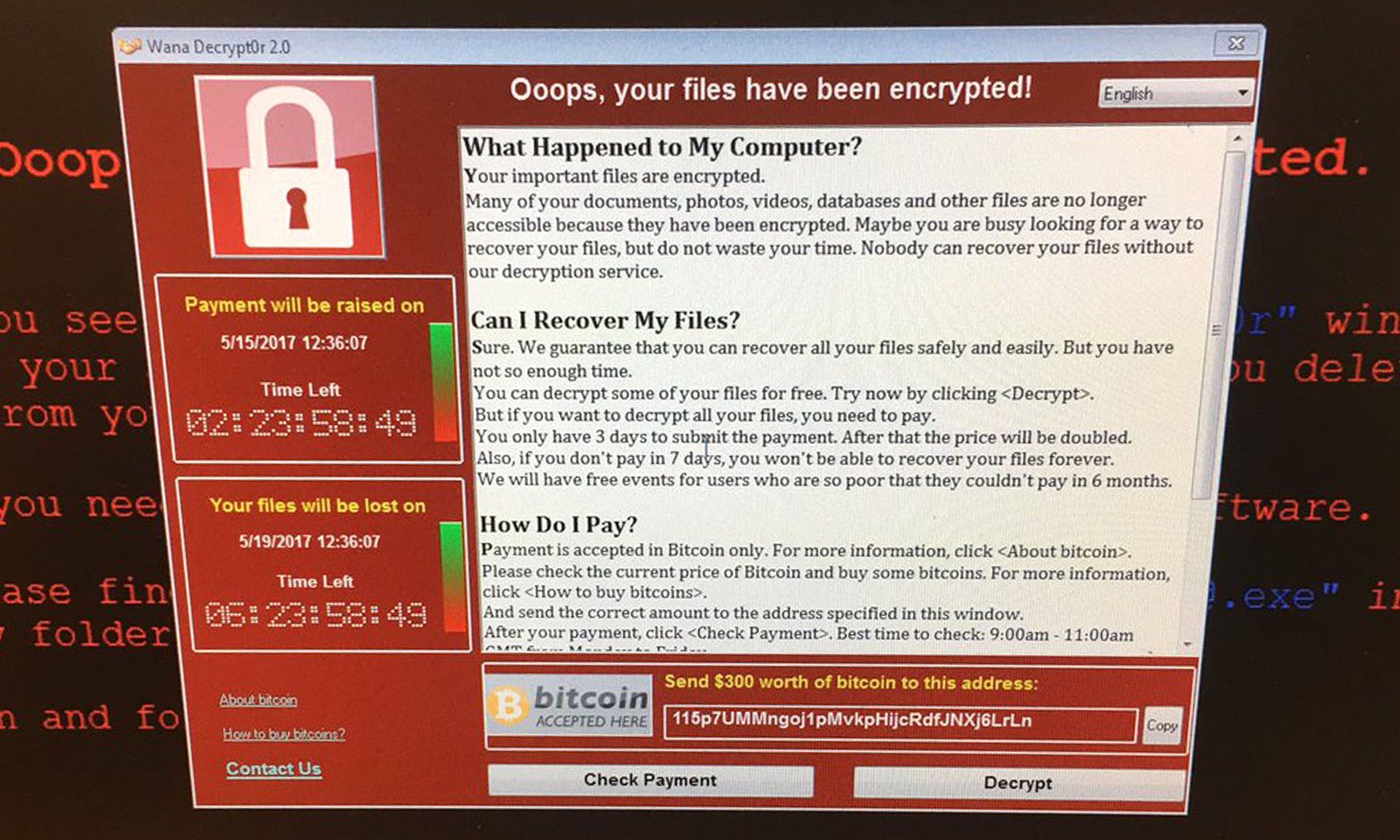
The malware attack, which has been named “WannaCry” (WanaCrypt0r 2.0, aka WCry), exploits vulnerabilities within Microsoft Windows locking users out of their files unless the administrator pays a hefty fee.
The malware encrypts files on the victim’s computer and then prompts the user for a payment of $600 in Bitcoin. Initially it was reported that the ransomware was asking for $300, but they seemed to have modified their coding. Alongside the payment request are two countdown timers. The first timer warns that the payment amount will increase if it expires and other timer, which is set for a longer period, warns that all files will be deleted if payment is not made at all.
This attack has wreaked havoc worldwide. In the UK, at least 16 medical institutions, including hospitals, were forced to shut down and turn away non-emergency patients until they could get systems back online.
Spain reported a large number of companies attacked, including telecommunications giant Telefonica (TEF.MC). Spain’s Computer Emergency Response Team issued a statement that several government organizations had been infected as well.
Russia’s ministry for internal security claims to have been hit as well, stating that 1,000 of its computers had been affected. MegaFon, one of Russia’s largest telecoms reported it had been hacked as well.
U.S. based FedEx confirmed today that it had been affected and was “experiencing interference.”
The Financial Times reports that the malware is likely the result of National Security Agency “digital weapons” that were leaked online last year by a group called the Shadowbrokers. According to Becky Pinkard, vice-president at Digital Shadows, a cyber intelligence firm, “They seem to have adapted one particular tool, Eternal Blue, and that would explain why this is spreading so fast.”

Kaspersky Lab, a Moscow based internet security company whose products are widely used in homes, businesses, and government agencies around the world, was the first to report on the attack. Kaspersky Lab has been under recent scrutiny by US intelligence because of their market position and possible ties to Russian intelligence services.
The intelligence community has warned repeatedly about increasing cyber threats. Just yesterday, before the U.S. Senate Intelligence Committee investigating Russia’s alleged meddling in the U.S. presidential election, Senator Marco Rubio (R-FL) asked top U.S. intelligence officials the following question about Kaspersky:
“And this is for all the members of the committee, as has been widely reported, and people know this, Kaspersky Lab software is used by not hundreds of thousands, millions of Americans. To each of our witnesses I would just ask, would any of you be comfortable with the Kaspersky Lab software on your computers?”
Acting FBI Director Andrew McCabe, CIA Director Mike Pompeo, Director of National Intelligence Dan Coats, NSA Director Michael S. Rogers, Director of the Defense Intelligence Agency Lt. Gen. Vincent Stewart and the Director of the National Geospatial-Intelligence Agency Robert Cardillo all answered with “no.”
At yesterday’s hearing Senator Joe Manchin (D-WV) also grilled the intelligence committee over the use of Kaspersky software.
Executives at Kaspersky have denied any links to Russian government. According to Buzzfeed a spokesperson for Kaspersky stated this week, “[Kaspersky] has no ties to any government, and the company has never helped, nor will help, any government in the world with its cyberespionage efforts. For 20 years, Kaspersky Lab has been focused on protecting people and organizations from cyberthreats, and its headquarters’ location doesn’t change that mission–just as a U.S.-based cybersecurity company doesn’t send or allow access to any sensitive data from its products to the U.S. government, Kaspersky Lab products also do not allow any access or provide any secret data to any country’s government.”

It appears that the malware exploits Windows based computers that haven’t received the Microsoft security patch released on March 14th. The patch covers vulnerabilities in not just the operating systems themselves but in applications including the Microsoft Explorer and Edge browsers, Microsoft Office applications, Adobe Flash Player, and even the Windows DVD Maker among others.
These updates are available on the following operating systems:
- Windows Vista
- Windows Server 2008
- Windows 7
- Windows Server 2008 R2
- Windows 8.1
- Windows Server 2012
- Windows Server 2012 R2
- Windows RT 8.1
- Windows 10
- Windows Server 2016
Currently, Kapersky Labs recommends installation of the latest patch from Microsoft and doing malware scans of your system. They have also of course recommended installation of their own scanning software as well.
There may be other systems and applications that could be vulnerable. The best thing to do is make sure your system is kept up to date with this latest security patch.
Joe Stone, Lima Charlie News
Joe Stone is an Army combat veteran having served tours in Guantanamo Bay, Egypt, and Afghanistan, as well as two tours in Iraq. After 15 years of service, Joe was medically discharged from the Army, returning to his home in Washington State. There Joe focused on his reintegration into civilian life through extensive civic engagement and veteran outreach, focusing as well on volunteering with local community groups and writing. Follow Joe on Twitter @JStoneLC
Lima Charlie provides global news, insight & analysis by military veterans and service members Worldwide.
For up-to-date Technology news, please follow us on twitter at @LimaCharlieTech
In case you missed it:



![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01-480x384.png)
![Image When fine art meets Bitcoin, blockchain and cryptocurrency the real fun begins [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/04/When-fine-art-meets-Bitcoin-blockchain-and-cryptocurrency-the-real-fun-begins-Lima-Charlie-News-480x384.png)
![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-480x384.jpg)
![Image Huawei – China’s telecom giant hits a giant wall [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/01/Huawei-–-China’s-telecom-giant-hits-a-giant-wall-480x384.png)
![Image U.S. 'Space Force' looking more and more like space reality [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/Space-Force-looking-more-and-more-like-space-reality-480x384.png)

![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01-150x100.png)