A group of U.S. Senators are currently attempting to push a bipartisan bill through the Senate which aims to address a growing number of public concerns over easily hackable Internet of Things technologies. The Internet of Things, or IoT as it is commonly referred to, is a broad term that refers to all devices and applications possessing the ability to connect to the internet. Today, this includes a vast and rapidly growing array of devices ranging from smart watches and household appliances, to internet connected vehicles, medical devices, and even smart homes.

In May, Lima Charlie News reported on the introduction of a Senate bill aimed at promoting innovation and development of Internet of Things technologies in the United States. The bill, dubbed The Developing and Growing the Internet of Things, or DIGIT Act, followed a January report by the US Department of Commerce called, “Fostering the Advancement of the Internet of Things.”
While these measures sought to weaken government intervention in IoT development and foster innovation, the new bill proposed on August 1st, aims to regulate IoT devices sold and used within the US government in hopes of addressing prominent security concerns. This call for tougher security follows a major Denial of Services attack against internet infrastructure firm Dyn last October and the subsequent emergence of the Mirai botnet. While most large scale malicious online attacks have used home and laptop computer IP addresses when recruiting for a DdoS attack, the Dyn attack was conducted by tens of millions of IP addresses from seemingly benign IoT cameras, baby monitors, and other household devices and applications.
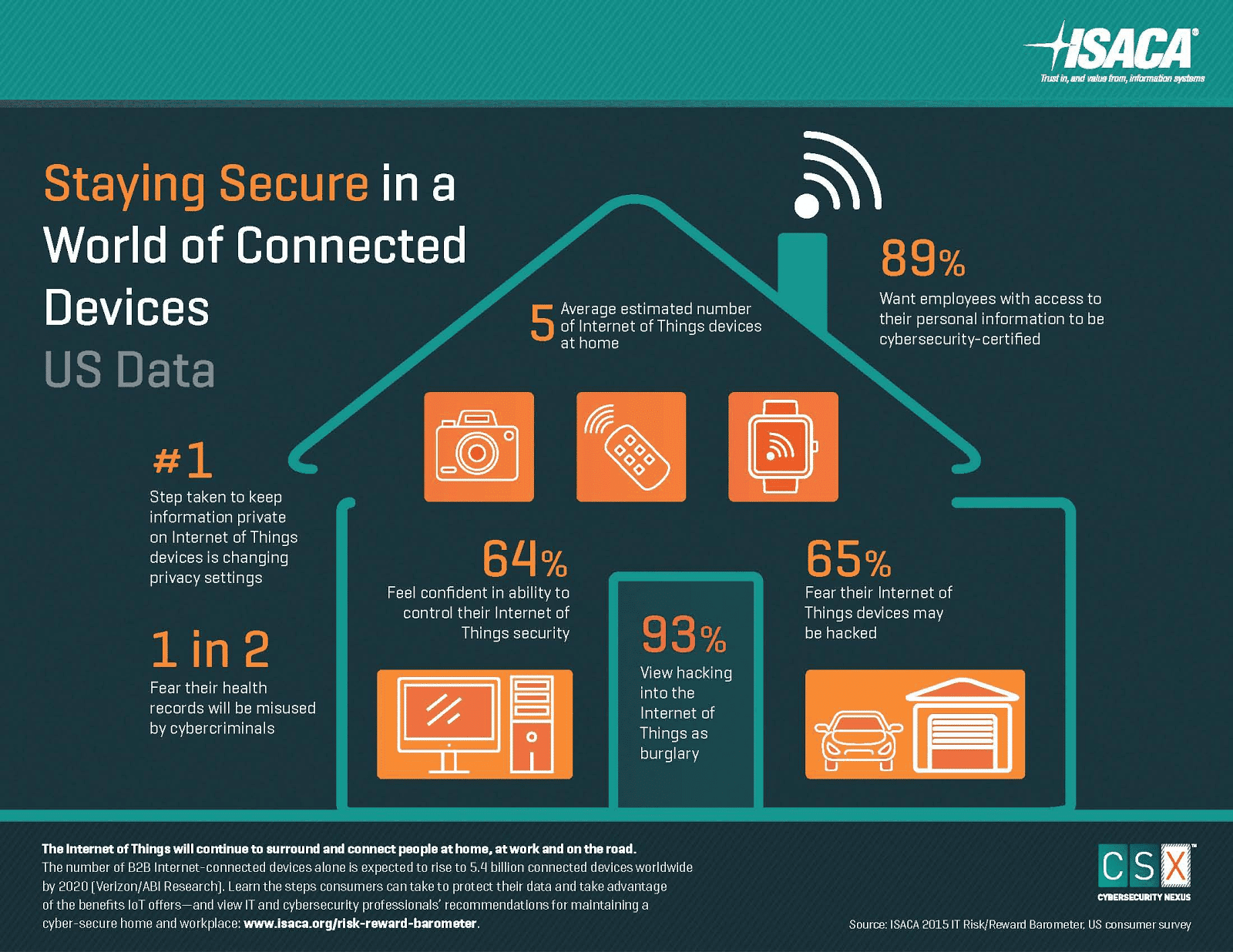
Since its inception, the Mirai botnet has weaponized IoT devices in a number of attacks including that of a prominent tech security journalist. These attacks, in addition to rising public paranoia following The Wikileaks Vault 7 data dump that exposed the CIA’s ability to hack smart TVs and manipulate webcams, has contributed to a fierce call for tougher security measures on rampantly insecure IoT devices.
The Internet of Things Cyber Security Improvement Act of 2017, co-sponsored by Senators Mark Warner (D-VA), Cory Gardner, (R-CO) Deb Fisher, (R-NE), Rob Wyden, (D-OR), and Steve Daines, (R-MT) looks to bolster government cyber defenses by demanding new security requirements for all devices. If implemented in full, the bill would require IoT device sellers to ensure that all products are patchable upon release, would prohibit hard set, have unchangeable passwords, and would demand devices be free of any presently known security vulnerabilities. Additionally, the bill would require all executive agencies to develop and maintain a publicly available database that lists all IoT devices in use and the names of their manufacturers. The bill also provides protection from criminal prosecution for “Good Faith” hackers who expose and report any potential device vulnerabilities.

Senator Mark Warner (D-VA) sought to reinforce the need for a bill that strengthens security measures without impeding innovation. In a statement, Warner said, “this legislation would establish thorough, yet flexible guidelines for Federal Government procurements of connected devices.”
Introduced a bill today creating #Cybersecurity standards for federal #IoT purchases. It's time to raise the bar for federal #IoTSecurity pic.twitter.com/GpgRm5OHQC
— Mark Warner (@MarkWarner) August 1, 2017
Colorado Senator Cory Gardner, one of the bill’s republican signatories, commented on the Senate’s attempt to reach across the aisle for security measures. “This bipartisan, commonsense legislation will ensure the federal government leads by example and purchases devices that meet basic requirements to prevent hackers from penetrating our government systems,” said Gardner.
While the government has been wary of dipping its toe into IoT regulation, security analysts have been quietly sounding their alarm bells. In a Washington Post article, Harvard lecturer and outspoken internet security speaker Bruce Schneier, warned that without government intervention, the market will not take action until it is too late. “The sellers of those devices don’t care,” Schneier said. “There is no market solution because the insecurity primarily affects other people. It’s a form of invisible pollution.”
In an interview with Lima Charlie News, Clinton Metu, (27) a Cyber Security Engineer Consultant at Booz Allen Hamilton, said that while he thinks a portion of the media coverage surrounding IoT vulnerabilities are sensationalized, the public does indeed face a great threat. Much of the problem, he says, comes from a lack of knowledge on the part of the consumer. “The average consumer doesn’t have the luxury of worrying about these IoT devices, because they aren’t deploying them in a secure manner, nor should that be expected of them.” The brunt of the burden for security, said Metu, should lie with the manufacture and not the consumer.
And while the recent Mirai botnet has proven the brutal efficiency of IoT devices when used in DDoS attacks, they might just be scratching the surface. For Metu, the true threat with IoT devices lies with bad actors who decide to use these technologies as a way to gain persistence within a network. Through a vulnerable IoT device a malevolent actor can access one’s home network and wreak havoc. From this type of attack the hacker could steal sensitive data to sell on the black market or keep as blackmail. This criminal technique, Metu says, “poses a huge, glaring risk to the confidentiality, integrity, and availability of any system they [the consumers] have connected to the same network as their IoT device.”
New green paper released today on what @CommerceGov can do to advance the #InternetofThings: https://t.co/fAveOTAuHV #IoT #DigitalEconomy pic.twitter.com/HGs0uqOlA0
— U.S. Commerce Dept. (@CommerceGov) January 12, 2017
The implications of an attack on a government agency network are far reaching and severe. Any regulation expanded to the public sector, however, may be met with stronger resistance. While the facts remain that IoT devices are largely undersecured, the sheer volume of emerging devices may present a challenging coordination issue. According to a January report released by the US department of Commerce, the number of IoT devices in the US alone are expected to double by 2020. This would amount to a sum of over 4.1 billion devices.
In lieu of additional government regulation, some argued that the path forward lies instead with additional technology and innovation. Currently there are a number of emerging IoT security technologies on the rise, including IoT authentication, IoT network security, IoT encryption, and IoT security analytics, to name a few.
Still, others may say that a more secure virtual network can best be accomplished through human education. While not foolproof, through proper updates and patches by users, many of the most accessible exploits can be easily guarded against.
Though the fate of the Internet of Things Cybersecurity Act is still unclear, Clinton Metu believes the measures being pursued by the US government may serve as a guiding example that the consumer market can follow; a market that he says currently resembles, “the wild west.”
Without any governing authority to enforce basic security measures, Metu believes IoT manufacturers are currently able to negligently release items onto the market with clear vulnerabilities. And though the individual is ultimately held accountable to some extent for all their choices and purchases, the IoT manufacturers currently have access to much greater information. While it is unlikely that the average consumer will have access to the type of knowledge necessary to properly secure their devices, Metu says, “it is very likely that the device manufacturer is going to have access to a security-minded developer who can lead the implementation of the security considerations.”
Whether through government regulation, technological advancement or consumer reeducation, a solution to securing future IoT devices is pressing and would affect a large swath of network connected peoples.
LIMA CHARLIE TECH, with Mack DeGeurin
For up-to-date tech news, please follow us on twitter at @LimaCharlieTech
In case you missed it:







![Image Memorial Day may soon be a remembrance of democracy and those who had the courage to defend it [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/05/Memorial-Day-may-soon-be-a-remembrance-of-democracy-and-those-who-had-the-courage-to-defend-it-Lima-Charlie-News-480x384.png)
![The Mind of Bolton - AUMF and the New Iran War [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Inside-the-mind-of-Bolton-Lima-Charlie-News-main-01-480x384.png)

