Over the course of two days, the cyber security company, Centrify, in collaboration with the Institute for Critical Infrastructure Technology (ICIT) welcomed over 400 of the world’s sharpest technical minds to CyberConnect 2017.
The conference, one of the largest of its kind this year, featured over thirty keynote speakers from the private industry, as well as leaders from government and military backgrounds. Over 500 security specialists and enthusiasts registered to attend the event in person at the Grand Hyatt Hotel in New York City. Additionally, over 1,500 viewers registered for the event’s lives steam, according to Centrify Co-founder and CEO Tom Kemp.

As the number of privileged accounts increases in any enterprise the risk of a costly breach rises. The managing of privileged credentials is an area of significant interest for Centrify. Image courtesy of Centrify.com
The Company
Centrify, headquartered in Santa Clara, California, began 13 years ago under the direction of Kemp, CTO Paul Moore and SVP of Engineering Adam Au. Since then, the company has seen a rapid rise in the security vendors industry. With regional offices in Seattle, Hong Kong, London, Munich, Brisbane and Sao Paulo, Centrify’s reach has gone global. The private company currently serves over 5,000 customers—among them, over half belong to the Fortune 50.
The security company stands out from the competition due to its single platform incorporation of Privileged Identity Management and Identity-as-a-Service. Unlike most of its competitors, Centrify is technologically diverse with a focus on inner-company-innovation. According to Kemp, Centrify features deep Mac and Mobile integration and fosters an environment that encourages competition and in-house innovation.



From left to right. CTO and Co-founder Paul Moore, Co-founder and CEO Tom Kemp and Co-founder and SVP of engineering Adam Au. Images courtesy of Centrify.com
According to Verizon’s 2017 Data Breach Investigations Report, over 81% of breaches are now leveraged, “either from stolen or weak passwords.” Of those breaches that do occur, over 73% are launched for financial gain. Victims of these attacks come from a variety of industries, including financial and healthcare organizations, retail and the public sector. Just this year, compromised credentials were responsible for attacks on companies like HBO, Equifax, and the Office of Personnel Management.
The issue of password insecurity was discussed at great length at the CyberConnect conference. With the average consumer required to enter information for a constantly growing number of accounts, the risk of highly insecure or repeated passwords goes up. People simply do not have the mental bandwidth to keep track of so many unique passwords.

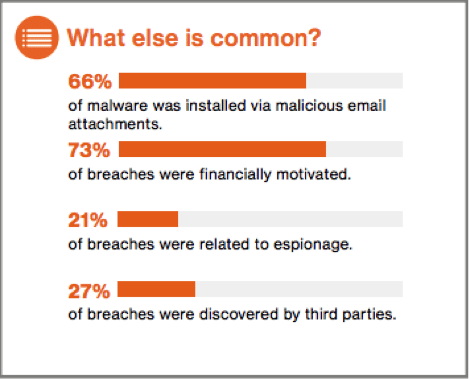
Verizon’s Annual Data Breach Investigations Report (DBIR) takes a deep dive into common attack vectors and paints a picture of cyber intrusion. Chris Novak, the report’s Global Managing Principal, broke down the company’s findings at CyberConnect 2017. Images Courtesy of Verizon.com
This constant onslaught of attacks by bad actors has led an increasing number of companies to seek outside security expertise. While some may turn to all-encompassing giants like Microsoft, Centrify Product Officer Bill Mann said that emerging enterprises do not want to be locked down to a single vendor.
“The cyber world is heterogeneous,” Mann said. Because of this, Mann believes people are more comfortable seeking out a third-party vendor like Centrify.
Since its inception, Centrify’s customer base has skyrocketed. The company reports having over 5,000 customers and receives funding from top-tier investment firms Samsung Venture Investment, Accel, Jackson Square Ventures and others.
A key component of Centrify’s success relies on their partnerships. By working alongside companies versed in cloud, mobile and Big Data, Centrify can offer a comprehensive and easy to use service. Centrify Alliance Partners include Apple, Amazon, Google, Blackberry, Dropbox, IBM and many more.
In addition to providing security services for some of the world’s leading private industry firms, Centrify also plays a critical role in providing security for government institutions and agencies at the local, state and national level. Currently these constitute roughly 20% of the company’s customer base, according to Kemp.
Centrify expects that government and military customers will increase over time. Although there used to be a stark difference in demand between the public and private sector, Kemp says that more and more government agencies are experiencing similar pain points and are requesting the same security products as large private firms. While providing services to governments previously involved multiples layers of complexity, the current differences are restricted mostly to regulations like the HSPD-12, according to Mann.
Whether serving governmental institutions or major private firms, Centrify focuses on being ahead of the curve in a security world where defensive tactics regularly lag behind ambitious attackers. To combat this, Centrify invests money and mind power into imagining innovative methods of security.
During his keynote speech at CyberConnect 2011, Mann noted the need for all companies to move to a Zero Threat Model. This method of security flips the contemporary periphery-based security on its head.
“Bad actors are already within our network,” Mann said.
CPO Bill Mann leads the conversation at #CyberConnect 2017. Building #Security into apps, Zero Trust Model, & Access in your Network. pic.twitter.com/66SYNsI7h0
— Lima Charlie Tech (@limacharlietech) November 6, 2017
Mann compared the old method of single factor authentication passwords to locking the front door of one’s home. These locks, however, can easily be broken.
“We need to be able to protect the asset as close as possible to the source,” Mann said.
For Centrify, the traditional password is truly a thing of the past. While the they presently encourage companies to continue implementing Multi-Factor Authentication in the short term, the future appears much more profound.
By using biometrics, artificial intelligence and machine learning technologies, Centrify looks to make credentials unique to individual users.
While Centrify is looking to stay a step ahead of the competition with credentials security today, the emergence of Internet of Things technology will make these methods a necessity in the near future.
Mann anticipates that eventually everything in any given building will become an IoT device. This presents some major security issues. With low costs of entry for developers, IoT devices are notoriously insecure.Mann also said that it is especially difficult to trace IoT devices to their original user due to their ephemeral, short lived server lives.
“We are looking at the problem of first identifying those devices and then deciding how to manage the privileges on those devices.” Mann said.
Due to a lack of standardization, IoT presents additional challenges to security professionals. Companies are rapidly integrating internet accessibility into nearly every product imaginable. According to a January report by the U.S. Department of Commerce, over 4.1 billion IoT devices are expected in the U.S. alone by 2020.
“The problem is that there are millions and manufacturers and millions of devices on the market and there is no standardized way with how to talk to these devices.”

While still in their infancy, Internet of Things technologies may fundamentally alter the way people interact with the world. A world of internet connected devices, however, requires a re-imagining of mass- scale cyber security.
According to Kemp, Centrify brought in over $100 million in sales last year. According to their CEO, the company has, “reached critical mass.” When asked by Lima Charlie whether or not the company looks to go public, Kemp said it was under consideration but that there are significant advantages to remaining private. Kemp said that remaining customer-funded offers the company flexibility. This flexibility has allowed them to become one of the leading names in cyber security.
Whatever the future may hold for Cyber defense, Centrify is sure to be leading the conversation.
LIMA CHARLIE TECH, written by Mack DeGeurin, edited by Tony Sklar
For up-to-date tech news, please follow us on twitter at @LimaCharlieTech
Lima Charlie provides global news, insight & analysis by military veterans and service members Worldwide.
For up-to-date news, please follow us on twitter at @LimaCharlieNews
In case you missed it:


![Image Intelligence Community mobilizes for Cyber War with Russia [Lima Charlie News][Photo: Mark Wilson]](https://limacharlienews.com/wp-content/uploads/2018/08/title-asldkfj-480x384.jpg)
![Image Singapore Summit leaves North Korea cyber threat off the table [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/06/Singapore-Summit-leaves-North-Korea-cyber-threat-off-the-table-Lima-Charlie-News-480x384.png)
![Image The Week in U.S. Politics [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/03/Lima-Charlie-Week-in-Politics-01-480x384.jpg)

![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-480x384.jpg)
![Image Huawei – China’s telecom giant hits a giant wall [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/01/Huawei-–-China’s-telecom-giant-hits-a-giant-wall-480x384.png)
![Image U.S. 'Space Force' looking more and more like space reality [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/Space-Force-looking-more-and-more-like-space-reality-480x384.png)
![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01-480x384.png)
![Image Intelligence Community mobilizes for Cyber War with Russia [Lima Charlie News][Photo: Mark Wilson]](https://limacharlienews.com/wp-content/uploads/2018/08/title-asldkfj-150x100.jpg)
![Image Singapore Summit leaves North Korea cyber threat off the table [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/06/Singapore-Summit-leaves-North-Korea-cyber-threat-off-the-table-Lima-Charlie-News-150x100.png)