Democracies worldwide are facing critical challenges from ever expanding cyberwarfare operations with the ability to not just threaten infrastructure, but to control information. Until recently, it was generally accepted that there were just five countries that had the capability of carrying out offensive and defensive cyber-warfare operations on a large scale – the United States, China, Russia, Iran and Israel. But that list has grown. Lima Charlie News presents an in-depth guide to the major players and programs that have deployed to the world’s Cyber Battlefield.
On November 2, 1988, Robert Tappan Morris, the 22 year old son of Robert H. Morris, Sr., launched what is considered the first computer worm to be distributed via the Internet. The Morris Worm, or Great Worm, once released slowed down infected systems to a crawl rendering the networks they ran unusable. Within hours, the Internet was largely disabled in North America, while the worm was making its way around the world. It would take nearly a week before the Internet was able to reconnect and become united again. Robert Tappan Morris would become the first person to be prosecuted and convicted under U.S. federal law for releasing the worm.
At the time, Morris’ father was the leader of an innovative new team at the National Security Agency (NSA). Morris Sr. would co-author a series of books for the U.S. Department of Defense and the NSA known as the “Rainbow Series”, computer security standards and guidelines that would help develop America’s earliest cyber warfare doctrines and tools.
When Morris’ son released the Great Worm, it was a significantly different time. In 1989, there were just 27 known computer viruses. Today, that number is in the millions. The prevention of attacks and enforcement against violators has become an increasing quagmire costing billions. Cyber attacks against U.S. businesses cost $654 billion in 2018 alone. And while all network connections are to an extent traceable, this can only be taken so far before things get complicated. The Internet is essentially ruled by functional anarchy, and those wishing to control it will find that it is much like herding cats. Network traffic patterns, in combination with encrypted tunnels and anonymity servers, means that it is near impossible to control things on a good day.
Even worse, if you try to trace criminal traffic across world networks things will quickly become political. It has become even easier to hide an attacker’s true identity or intent by using proxies in nations that are less than cooperative with Western law enforcement agencies and counter-cyberterror efforts.
Attempts to trace an attack can be faltered with ease when traces require the cooperation of China, Iran or Russia. The refusal to assist with requests for data passing through their national networks leaves the case cold. It doesn’t help that attacks are often suspected of originating from state-sponsored or even state-operated outfits within those nations.
I do not know with what weapons World War III will be fought, but World War IV will be fought with sticks and stones.”
– Albert Einstein
The Great Worm to Cyber Warfare
Cyber warfare is an extremely cost-effective means of disrupting or disabling an opponent. With far less reliance on large-scale industrial capabilities, the new battlefield of the digital era relies on the availability of key individuals with particular skill sets and mental aptitudes. In this new domain, smaller, often poorly funded players can effectively strike much more powerful, well-funded foes.
This type of warfare also has additional advantages to traditional asymmetrical or even symmetrical warfare. It can be extremely difficult to trace an attack back to the originating attacker. While seldom of importance to small asymmetrical terror-oriented groups, like al Qaeda’s cyber warfare wing or the pro-Assad Syrian Electronic Army, that advantage is key to state-operated or state-sponsored groups seeking to mask their attacks.
A prime David vs. Goliath example is Palestine. Under the leadership of Iran-supported Hamas, Palestine is engaged in a protracted cyberwar with a significantly better-funded U.S.-supported Israel. Israel has in turn successfully attacked its other traditional foe, Iran, on multiple occasions with great success and accuracy utilising its cyber warfare capabilities.
The chief example of Israel’s offensive cyber warfare capability is the so-called Stuxnet computer worm attacks against the Supervisory Control and Data Acquisition (SCADA) systems of Iran’s nuclear program in 2010. It is believed that these attacks, which exploited a well-known vulnerability in Microsoft Word, were the breaching point of Stuxnet’s designers to propagate a larger, system and network-wide infection. The Stuxnet attack is widely believed to have employed a joint US-Israel designed cyberweapon that had begun development in 2005 with the specific objective of disabling Iran’s nuclear capabilities.
While Stuxnet appears to have been successful, the wide distribution of the worm led to other groups using it as part of their own cyber attack toolbox under a variety of deviations and names. This may include use by Iranian-backed groups.
Triton, believed to be a version of Stuxnet developed by an unknown third-party group, was deployed in December 2017 against an unidentified power station in the Kingdom of Saudi Arabia. Triton breached the plant’s security measures utilising a very similar method as the original Stuxnet worm, and disabled the power station’s Triconex industrial safety technology (made by Schneider Electric SE). As a result of this attack, the power station’s personnel had to manually override the security systems and shut it down, causing a minor, largely localised disruption in the power grid.
While that attack was not serious, it was a good proof of concept. It would take until the end of 2015 before that proof-of-concept was deployed on a large scale.
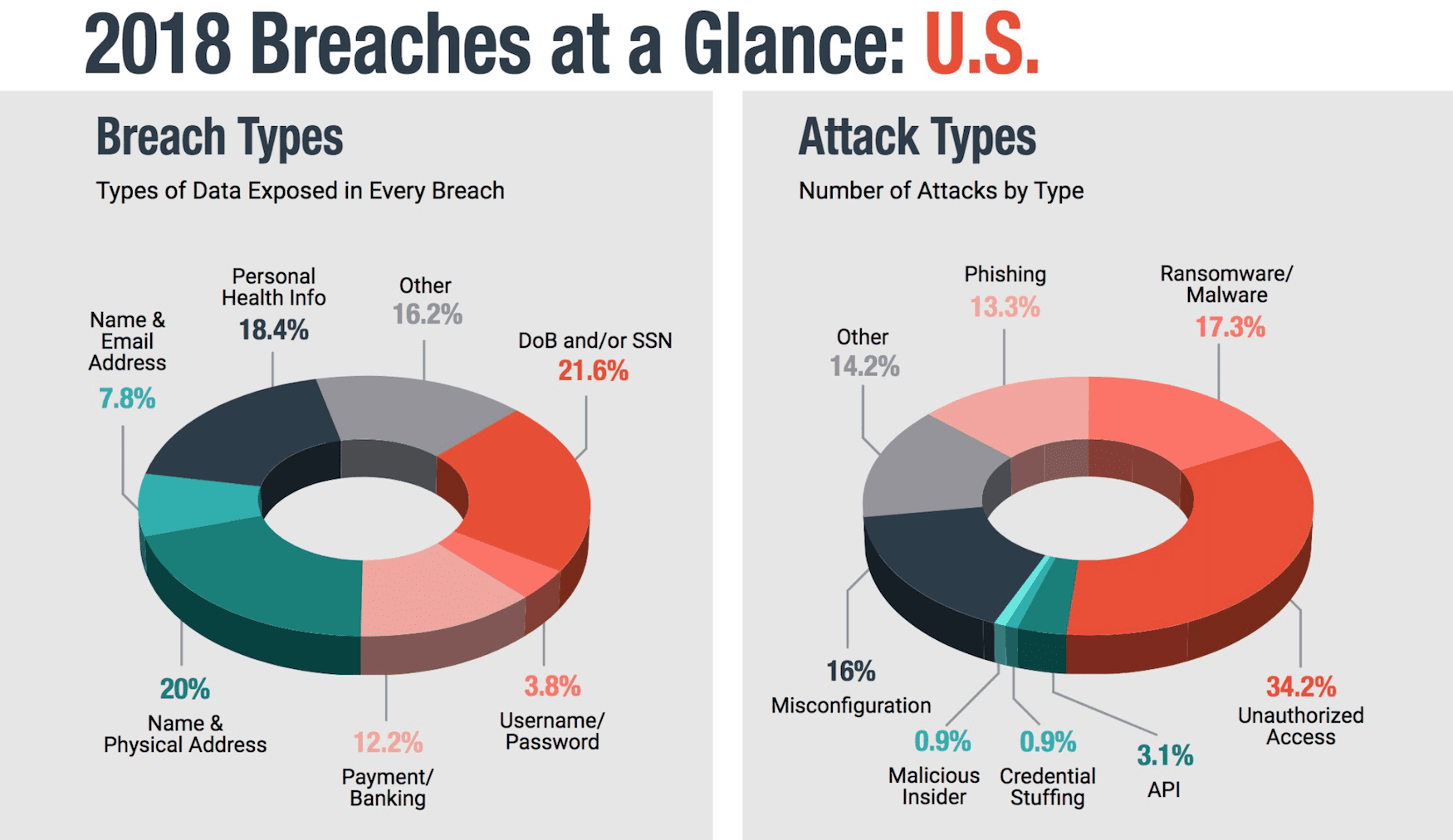
As a result the group gained access to 30 substation SCADA controls which they used to switch the power off to 230,000 homes just before December 24th. With cyber conflicts having no rules of engagement to dictate even a modicum of humanity, thousands of households faced the bitter cold of a Ukrainian winter.
To cover their tracks, and to make bringing the stations back online even more difficult, the hard drives of several key computers were wiped out using the KillDisk malware. Whole segments of the internal IT-infrastructure were shut down. Service technicians would have to travel to each individual, often remote substation to reinstall or replace the control installations. It would take up to 6 hours before the systems were restored. Similar, but not yet successful attacks on the U.S.-power grid appear to be frequent.
As global cyber threats have continued to advance and expand in scope and complexity, within the past five years, Western nations have begun to wake up to the realisation that cyber activities from foreign operators can even endanger the very foundation of democracy. From the 5G network concerns with Chinese tech giant Huawei, to the ongoing discourse regarding aggressive Russian interference in American and European elections, the West has realised that safeguarding democratic values requires active engagement as much on the human terrain as on the cyber battlefield.
The Big Five of Cyberwarfare
In 2009 it was generally accepted that there were just five countries that had the capability of carrying out offensive and defensive cyber-warfare operations on a large scale: the United States, China, Russia, Iran and Israel. In 2019, ten years later, that list grew to include the United Kingdom, North Korea and Vietnam. The United Arab Emirates (UAE) is believed to be about to join the list as well. On a more tactical level, Syria, Lebanon and Germany are believed to be able to carry out targeted attacks.
The original five will for the foreseeable future continue to be the world’s primary cyber warfare actors.
USA (America First)
The United States of America is the oldest great cyber power with a strategic-level capability to not just carry out cyber attacks, but to defend against attacks on an open-war level. It is also one of the nations in the top five whose economy and social infrastructure are the most dependent on the Internet. Disruptions in the U.S. network could quickly prove devastating to all levels of its vital infrastructures.
As such, the U.S. has long prepared its offensive capabilities in a first-strike capable fashion, developing significant cyber capabilities. As far as defensive capabilities, the U.S. military and intelligence community quickly saw the need to divide the Internet – ARPANET for public use and MILNET for the relatively more closed off section.
However, the built-in defences implemented during the early days of the Internet were largely based on the notion of obfuscation rather than firm security measures. This approach was quickly proven to be inefficient, especially when even the so-called Morris Worm was able to make the jump from the public, academically oriented ARPANET, onto MILNET to infect systems.
This would lead to then-Vice Admiral John Poindexter suggesting in 1985 the introduction of a new security classification, “Sensitive but Unclassified” (SBU). The classification was intended to be implemented primarily on open academic research and fit below the usual levels of Top Secret, Secret and Confidential, while enabling the U.S. government to deny foreigners access to research on matters it perceived could be made sensitive if taken in a particular direction. One of the things Poindexter stated that would be labeled as SBU were research papers relating to what would become the Internet, and the U.S.-infrastructure of the networks which would come to encompass the Internet. The academic world rioted against the notion of being supervised by the cloak-and-dagger crowd. In the end, SBU would come into existence but it would only be applied, and then only sparsely, to research and related matters that were under explicit federal supervision and control. This was not at all near the grand scale that Poindexter had intended.
Throughout the 1990s, the U.S. worked to enhance its capabilities with the understanding that it would soon be forced to meet an enemy unknown on the cyber battlefield. However, the various agencies and units involved in these activities were largely held separate, with little overlap.
The CIA, which was quickly developing an impressive cyber offensive and espionage capability, did its thing separate from the NSA. The military would even divide its cybersecurity thinking and responsibilities to a regional, at times even localised, level under the control of base commanders. The Pentagon would, for a long time, merely advise bases on best practice rather than establish a common structure.
During this time, cyber attacks on U.S. military installations would be investigated by the Federal Bureau of Investigation (FBI), rather than the military intelligence division, despite the fact that the majority of attacks originated from inside Russia. The most famed such attack was the so-called Moonlight Maze attack in 1998, which managed to penetrate several sensitive U.S. government networks. That attack led to Newsweek reporting in September 1999 that the U.S. was “in the middle of a cyber war.”

America’s Post 9/11 ‘Big Brother’
After the attacks on September 11, 2001, as the War on Terror began, it was apparent that the U.S. was in danger of being attacked by small non-state actors on a grand scale as well. Al Qaeda was attracting capable, often young people, with considerable knowledge of how to carry out cyber warfare and cyber terrorism as well as affiliated influence operations. At the same time, the threat from old and new state actor foes was emerging. Russia, China and Iran were all getting into the game with a vengeance.
This led to several controversial knee-jerk suggestions by the U.S. security community.
In early 2003, now-Admiral John Poindexter, the former National Security Adviser to the Reagan administration, and then-Director of the DARPA Information Awareness Office (IAO), suggested a large scale project called “Total Information Awareness” (TIA). This “Manhattan Project of Counter-Terrorism” would entail the constant automatic monitoring of all American citizens. This would enable the system, and its analysts to detect could-be persons of interest with the intent of anticipating and preventing criminal acts before they were even committed.
In 2003, the project was defunded by Congress, only to be renamed the “Terrorism Information Awareness” project. With a name like that, no one could refuse it. Yet certain changes had to be made to make the sale. In 2004, the Department of Defense (DoD) had it funded under a classified budget annex. The TIA project team members were transferred to the NSA which would supervise the new iteration of the project.
Now, the politicians argued, the purpose was to limit the project to only target military and foreign intelligence interests against non-U.S. citizens. This, of course, meant that the project would have to be even less privacy aware [1], as you can only know if a potential threat is of foreign origin after you have analysed it in detail. Since 2006, TIA has largely been operating as a classified in-house project at the NSA. Similar projects, such as Topsail and Basketball have also come under NSA umbrella.
Many of these projects, such as Topsail, were mainly developed on spec by the Science Applications International Corporation (SAIC) in Reston, Virginia, with the help of the IAO under the name Project Genoa II. The SAIC board has the retired Admiral Poindexter as an adviser. Its former head of technology, Deborah Lee James, served as the Secretary of the Air Force between December 2013 and January 2017. Mrs James has been a voice in favour of increased military-related expenditures and has named Russia as “the biggest threat” to U.S. national security.
In 2009, a joint task force designed to coordinate the U.S. cyber warfare activities and be the tip of the spear was created – United States Cyber Command (USCYBERCOM). The command is situated at Fort George G. Meade in Maryland. The base is shared with the NSA, among other similar outfits.
Iran (Not Your Father’s Persian Techno)
Cyber warfare has long been a part of Iran’s military strategy, and is considered a part of the Iranian Revolutionary Guard Corps (IRGC) “soft war” operations. It is under this header that the support of foreign militia groups, and drop-in Islamist political parties, et al., can be found. Examples include Hezbollah in Lebanon, the al Houthi movement in Yemen, and Hamas in Palestine. All have their own cyber warfare operative units, often trained directly by experts from Tehran.
For instance, the Iranian Cyber Army, famed for its disruption of Twitter in 2009, is largely believed to be controlled by the IRGC. However, Iran appears less reliant on seemingly external, or named, groups than most of its contemporaries. Instead, Iran appears to prefer that the majority of its cyber operations exist under the direct command of the IRGC or one of its domestic national defence organs.
Israel has no doubt observed Iran’s growing offensive cyber capabilities with great concern.
In October 2013, the Iranian commander of the IRGC cyberwar division, General Mojtaba Ahmadi, was found dead in a wooded area near the town of Karaj, north-west of Tehran. Two 9mm rounds were lodged in his upper torso. The Tehran leadership immediately accused Israel’s external intelligence agency, the Mossad, of having carried out the killing.
Less than a week later, in mid-October 2013, the IRGC Brigadier General Mohammad Hossein Sepehr stated that Iran’s was the “fourth biggest cyber power among the world’s cyber armies.” The statement was agreed to by the civilian Israeli National Security Studies (INSS).
A July 2018 report by the American cybersecurity company FireEye detailed a suspected influence operation which originated from Iran. The operation aimed at individuals in the U.S., U.K, Latin America and the Middle East with the intent of leveraging a network of inauthentic news sites and supportive social media accounts to create anti-Saudi, anti-Israeli, pro-Iran and pro-Palestinian drive. Such behaviour was previously largely only attributed to Russian cyber influence and political warfare operations. A May 2019 New York Times article reported that despite FireEye’s 2018 report, these activities continued unhampered and with a degree of success.
Just last week, in the midst of escalated tensions over Iran’s downing of a U.S. drone, USCYBERCOM announced that it had engaged in a cyber offensive against an Iranian intelligence group believed to have assisted in the disabling of oil tankers near the Strait of Hormuz.
Read my statement on Iranian cybersecurity threats below. pic.twitter.com/qh7Zp9DBMY
— Chris Krebs #Protect2020 (@CISAKrebs) June 22, 2019
Israel (Israeli Beach Party)
To read about Israeli capabilities, please check out the Lima Charlie News article “Israel-Hamas Cyberwar, when old warfare meets new” (May 11, 2019).
China (Might Makes Right)
China is without a doubt one of the more active cyber warfare actors. This is no surprise, as China was one of the earliest adopters of the doctrine as it evolved. With China having both the world’s second-largest economy, and the second-largest defence budget, both after the U.S., it also has the resources to be a real contender on the cyber battlefield.
Chinese military strategists were impressed by the use of information warfare by the U.S. military and intelligence agencies during the first Gulf War, such as its effectiveness in causing the Kurds to riot against Saddam Hussein. This included subsequent U.S. operations in Kosovo, Afghanistan and again in Iraq. It was self-evident based on results that this new umbrella warfare term would play a critical role in the increasingly interconnected world.
In 1993, two years after the first Gulf War, China’s military strategic guideline, “Preparations for Military Struggle” (PMS), would include the line “winning local wars in conditions of modern technology, particularly high technology”. This was the first, careful step, of China’s venture into the world of modern warfare. By 2004, one year into the second Gulf War, the PMS was changed to read, “winning local wars under conditions of informationization”. The term informationization is a China-specific term which would further be defined in the 2004 Chinese National Defense plan. That plan has a paragraph which reads “informationization has become the key factor in enhancing the warfighting capability of the armed forces.”
In essence, China intended to use information warfare, which they would come to refer to as Cyber Warfare in their 2015 Military Strategy plan, to maximize their strategic capabilities without firing a shot. To best facilitate this, the Chinese Communist Party (CCP) set up its cyber warfare capabilities to work in tandem with the nation’s quickly growing industrial capabilities. This meant a focus on cyber espionage.
Down with CCP
In March 2019, the Swedish intelligence and research agency, Defence Research Agency (FOI), published a report titled “Kina’s industriella cyberspionage” (“China’s industrial cyberespionage”). The report was written by a team of intelligence analysts and consultants under the leadership of Johan Englund. It is the first public report by a government intelligence agency that details China’s increase in recent years of state-sponsored industrial cyber espionage, focusing on gathering information on next-generation IT-infrastructure equipment, missile technology, space and aeroplane technology.
In the report the FOI team shows that the Chinese cyberwarfare division is largely operated directly by the Chinese People’s Liberation Army (PLA), with the assistance of the Ministry of State Security (MSS). In addition, the CCP is increasingly becoming dominant within the Chinese corporate section. In fact, it appears that the CCP is pushing legitimate, non-state aligned companies aside if they are operating within the IT-infrastructure or high technology fields.
In essence, if you want to be in business, you must have the CCP involved along with its strategic interests. Huawei and ZTE are both listed in the report as a primary example of this.
While the Chinese cyber warfare division, under PLA and MSS control, is largely focusing on corporate and industrial espionage, the United States is not the only target. European and Asian nations have not fared much better. For instance, Australia, Canada and India have all claimed that Chinese government sponsored, probably controlled, hackers breached security protocols in 2013 and 2014 to secure access to blueprints of sensitive installations and intelligence research matters.
The number of attacks the U.S. government and private enterprises lay at the feet of China is numerous. While most appear to be targeting information hubs, such as attempting to gain access to the Google mail services, or installing spy-ware enabled firmware on CISCO routers before they leave the factory, some attacks have had lethal consequences in the “real” world.
For example, between 2010 and 2012, the PLA-MSS cyber unit was able to penetrate a vital CIA instant messaging and database system. This led to, the U.S. government claims, the deaths of between 18 and 20 CIA assets at the hands of Chinese government operators. A joint operation by the CIA and FBI resulted in the January 2018 arrest of a former CIA employee believed to have turned Chinese Spy, Jerry Chung Shing Lee. China has denied all accusations that it carries out offensive cyber warfare operations and has on a number of occasions accused the U.S. of doing the same against Chinese interests.
Yet, while China’s cyber espionage operations are aggressive in nature, it appears to be Russia that is on the largest offensive when it comes to disruptive cyber operations.
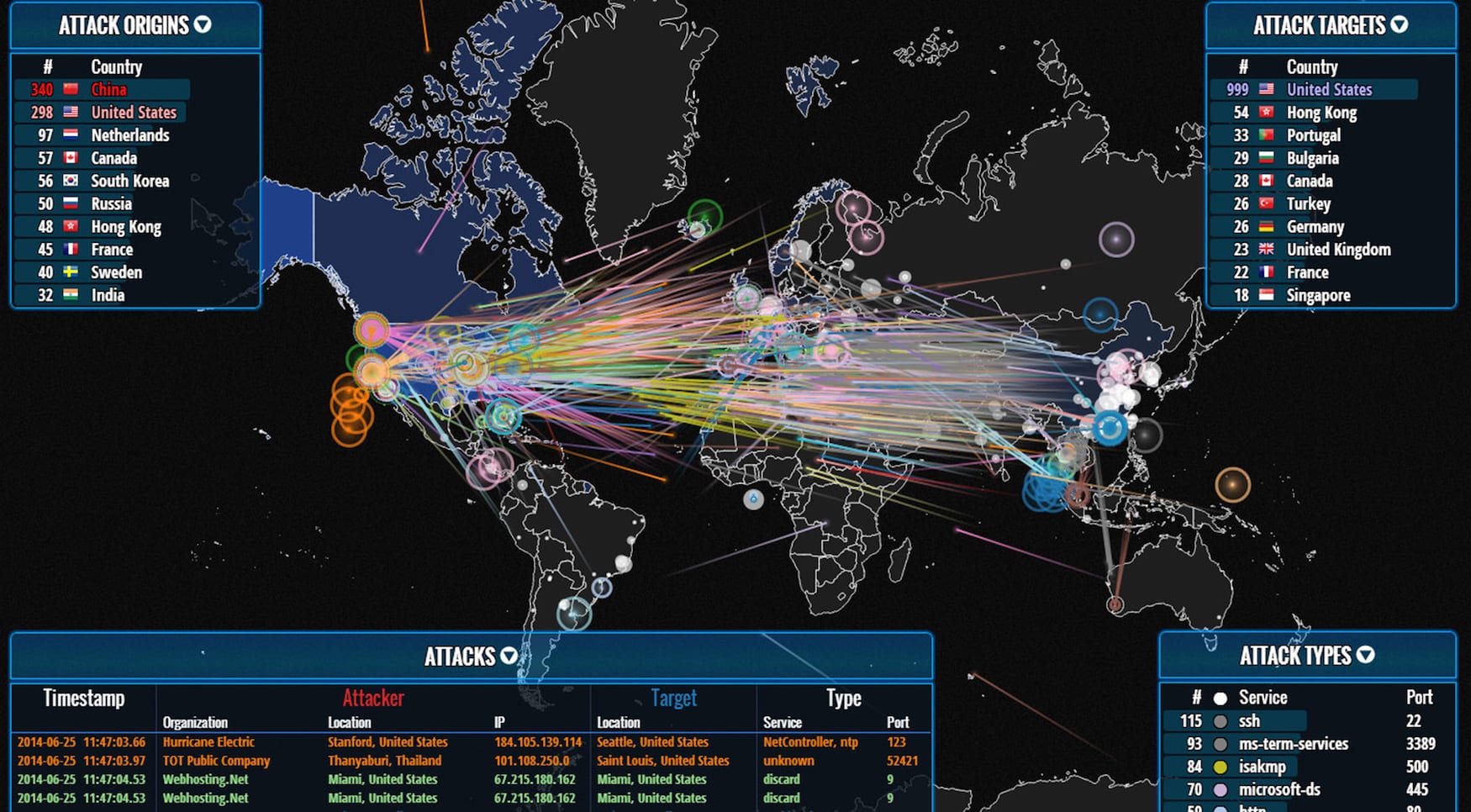
In August 2016, GRU officers targeted … a voting technology company that developed software by numerous U.S. counties to manage voter rolls, and installed malware on the company network. Similarly, in November 2016, the GRU sent spearphishing emails to over 120 email accounts used by Florida county officials responsible for administering the 2016 U.S. election. The spearphishing emails contained an attached Word document coded with malicious software … that permitted the GRU to access the infected computer.”
–Mueller Report, Vol. I, pg. 51
Russia (You’ve got mail from Boris.Badenov@Kremlin.ru)
The Russian intelligence services GRU (Glavnoye Razvedyvatel’noye Upravleniye), SVR (Sluzhba Vneshney Razvedki Rossiyskoy Federatsii), and FSB (Federal’naya Sluzhba Bezopasnosti Rossiyskoy Federatsii), are all highly active and on the offensive across the digital battlefields. Both the military and civilian intelligence services have had vital portions of their cyber operations exposed in recent times. Names of operators, internal unit designations and a wealth of confidential information have been released to the world. There is little doubt what the Kremlin is doing.
While there are, obviously, no official numbers on how many groups that the three Russian security services are either operating or to some extent controlling, it is widely believed that there are at least ten unofficial cyber warfare groups within the purview.
The outfit that carried out the Ukraine power grid attack in 2015, Sandworm, also known as SandWorm Team, is believed to be part of Russia’s emerging hybrid warfare and cyber warfare doctrine and directly sponsored by the Russian state. Sandworm along with Fancy Bear are both believed to belong to a particular cyber warfare division within the GRU, the military intelligence agency.
One of the premier Russian hacker signatures, Guccifer 2.0 has been tied to the GRU as well. Guccifer 2.0 became known for the so-called “DNC Hack”, the 2016 Democratic National Committee email theft which appeared on Wikileaks.
In March 2018, details from the Mueller investigation leaked attesting that Guccifer 2.0 was in fact a collective of persons working for GRU’s Unit 26165 and Unit 74455. This after server logs revealed that on at least one occasion someone utilising the Guccifer 2.0 persona had failed to activate a Virtual Private Network (VPN) to obfuscate his IP address. It was then revealed to investigators that his connection originated from a computer at the GRU headquarters on Grizodubovoy Street in Moscow.
On July 13th, 2018 the U.S. Department of Justice (DOJ) acted on the Mueller investigation findings and indicted 12 Russian intelligence officers, all of which had utilised the Guccifer 2.0 persona to carry out their activities. The individuals on the DOJ indictment list were Viktor Borisovich Netyksho, Boris Alekseyevich Antonov, Dmitriy Sergeyevich Badin, Ivan Sergeyevich Yermakov, Aleksey Viktorovich Lukashev, Sergey Aleksandrovich Morgachev, Nikolay Yuryevich Kozachek, Pavel Vyacheslavovich Yershov, Artem Andreyevich Malyshev, Aleksandr Vladimirovich Osadchuk, Aleksey Aleksandrovich Potemkin, and Anatoliy Sergeyevich Kovalev. The Russian government has, however, declined to extradite the people named and shown little inclination towards reconsidering its position.
SVR and FSB are seemingly equally active in the field as well.
The Russian hacking group “Turla Crew”, which has been active for at least 15 years, appears to be tied with both SVR and FSB. Turla Crew appears to specialise in espionage, information gathering, and placement rather than outright disruptive activities. Between 2013 and 2015 they appear to have focused intently on European government installations, such as secretaries’ computers, embassy computers and military installations. The fact that the group has been active for at least 15 years, and during that time deployed at least 15 different, highly advanced Trojan horses and computer viruses, could be an indicator of how well protected they are.
One of the most telling tools of Turla Crew’s design is Uroburos. The tool suite belongs to the so-called advanced “rootkit” line of tools, used to infect networks using proprietary techniques with the goal of setting up rogue Peer-to-Peer (P2P) networks, which it can then use to set up an ad-hoc network of infected nodes to covertly distribute or store confidential data. It is believed to have been active for three years before it was discovered by Western cybersecurity specialists. Pierluigi Paganini, a member of the European Union Agency for Network and Information Security (ENISA) and Cyber G7 Group stated in 2014 that he believed it could be a complex part of Russia’s cyber weapons programme.
In 2014, the Computer Network Attack (CNA) team at the joint Dutch intelligence task force, Joint Signal Intelligence Cyber Unit, was able to turn the tables on the Russian hacker group known as Cozy Bear. For more than three years the CNA team, which consists of members from both the civilian intelligence agency AIVD (Algemene Inlichtingen-en Veiligheidsdienst) and the military intelligence agency MIVD (Militaire Inlichtingen- en Veiligheidsdienst) had unfettered access to computers used by the Russian hacker group. During this period, the CNA was able to determine that ten individuals worked as part of the Cozy Bear group and that they were located inside the SVR headquarters.
In fact, the CNA had so thoroughly infiltrated the Cozy Bear group’s equipment that they had access to a built-in camera in the desk VoIP phone. Through that camera, the Dutch intelligence group was able to stream video and take pictures of visiting, ranking SVR officers.
Thanks to the evidence gathered during those three years by the Dutch cyber warfare division, the American intelligence community (USIC), including the CIA and the NSA, were able to convince several NATO allies that Cozy Bear was not only affiliated with the Russian intelligence apparatus, but had at times penetrated sensitive NATO installations.
In February 2017, it was discovered through an internal security review that Cozy Bear and Fancy Bear had made several attempts over a six-month period to breach network integrity at the Dutch Ministry of General Affairs and several other Dutch agencies. Rob Berholee, the head of the civilian intelligence agency AIVD, stated that they had concluded the attacks to have originated from Russia and had been seeking to gain access to privileged government documents. Fearing that a breach had occurred, but had remained undetected, Ronald Pasterk, the Dutch Minister of the Interior, declared that the 2017 Dutch General Election votes would be counted by hand. The Dutch intelligence agencies also warned that they had found evidence that the two Russian hacking groups had attempted similar breaches against French and German governmental server systems.
Cozy Bear, Fancy Bear and Guccifer 2.0 have all been directly linked to the DNC e-mail leak during the U.S. 2016 election.
Appearing before the U.S. House Committee on the Judiciary, on June 20, 2019, Dr. Alina Polyakova for the Brookings Institution testified that, “Russian influence operations do not focus on isolated events. Rather, taken as whole, they are at the core of a political strategy—honed in Europe’s East and deployed against the West—to weaken democratic institutions, sow discord in societies, and divide the transatlantic alliance.” Polyakova detailed ongoing cyber operations against Western / European nations, that included France, Germany, and Ukraine’s election systems and infrastructure.
"The Russian government is engaged in political warfare against the West. Its intent is to undermine trust in democratic institutions, values, and principles, which the Kremlin sees as a threat to its own authoritarian model," @apolyakova tells Congress. https://t.co/CZVK6Pic2W pic.twitter.com/DoV6KOWZcY
— Brookings Foreign Policy (@BrookingsFP) June 20, 2019
Known Methodology = Known Actors
The methodologies applied by both the Russian and Chinese hacker groups are, in essence, virtually identical with those utilised by the more advanced criminal hacker organisations. These focus mainly on economic hacking and the use of digital mercenaries operating on a commission from others. This is partly why it is exceedingly difficult for investigators to prove conclusively that alleged attacks, such as Stuxnet, come from state-sponsored or controlled entities, as opposed to private interests.
The primary difference can, however, be found in the level of professionalism and purpose that government-affiliated hackers display. They are more often than not seeking access to government or research systems, where the economic benefits of control are slim but the information benefits are interminable. This behaviour and selection of targets indicates nation-level espionage intents, which is seldom something that private organisations or non-commissioned individuals would be interested in.
Overall, these operations in the relatively new combat of cyber space are largely steeped in long-standing traditions, such as the tradition of Maskirovka.
Maskirovka: The Russian Art of Deception and War
One of the aspects that Iran, China and Russia all share, is the use of offensive cyber technologies in the art of gathering information and utilising that information to create disruptive deception. This methodology can be summarised in the Russian term “Maskirovka” – although this behaviour obviously predates even that defined practice.
The literal translation of Maskirovka means “disguise” and refers to the early-twentieth-century Russian military doctrine which encompassed deception and obfuscation intermixed with aggressive military operations to accomplish strategic as well as tactical objectives. While the doctrine has been applied as a tactical instrument by the Russians since the Battle of Kulikovo in 1380, it is not a Russian contraption in origin.
Seemingly the approach was defined by the Chinese in the 5th century BC. Found in the military strategy philosophical syllabus The Art of War, it was written by an amalgam of Chinese military strategists but widely attributed to General Sun Tsu. In it, the strategy is largely defined as turning one’s weaknesses to strengths by tightly controlling the enemy’s perception of your capabilities. This will then lead your foe to focus his forces and movements on the wrong capabilities in your arsenal.
Sun Tsu (or Sun Tzu) and his affiliates belonged to the so-called master thinkers (School of Zi), which came to define China’s “Hundred Schools of Thoughts”-era. It spanned the so-called Spring and Autumn and Warring States periods of 722-277 BCE. Other philosophers from the same school, such as Confucious (also known as Kongzi), who inspired Confucianism and the Six Arts concept, and Lao Tsu (Laozi), who inspired Taoism, would come to encompass similar thoughts of turning perceived weaknesses to strengths. This concept is also a recurring theme in other Far East military strategy-related philosophies, often under the guise of martial arts with all-encompassing philosophical aspects, such as the Japanese Budō.
“Every society is three meals away from chaos”
-Vladimir Lenin
The West Awakens – Democracy Targeted
Lima Charlie News has written extensively about cyber attacks and cyber influence operations that threaten the very foundation of democratic institutions worldwide. In addition to the Russian interference operations detailed in the Mueller Report, ongoing operations throughout Europe and the former Soviet Republics have awakened the U.S. and its NATO allies to the fact that safeguarding democratic values and elections requires active engagement on all fronts.
Most recently, reports have surfaced that USCYBERCOM has aggressively stepped up the deployment of cyber tools within Russia’s infrastructure, including systems operating the nation’s power grid, on new authorities granted by the White House and Congress (“defense forward”). According to the NY Times, a senior intelligence official speaking on condition of anonymity stated, “It has gotten far, far more aggressive over the past year … We are doing things at a scale that we never contemplated a few years ago.”
In Europe, a recent Finnish raid on what is likely to have been a joint Russian cyber and tactical operations cell headquarters inside Finland’s territory, is an alarming example.
On September 22nd 2018, Finnish authorities declared a no-fly zone over an archipelago of islands along the country’s southwestern coast, some 180 kilometres from the capital of Helsinki. This was followed by a large-scale raid by the civilian authorities acting on intelligence retrieved by the Finnish military Intelligence Division. Over a hundred heavily armed police officers, along with 280 individuals from other government organisations, descended on the small islands. To reach the area, the civilian authorities utilised military provided helicopters and naval vessels that had just received a fresh coat of paint to show that they were not, for the day, in military service. Still, the logistical aspect of the operation was carried out by military personnel on loan to the police for 72-hours.
The target was a series of buildings situated on the islands which were owned by a Russian corporation. Originally, the raid was described as being aimed at a Russian money-laundering operation. Information indicates, however, that the structures, one of which featured a helicopter pad and a private harbour, were believed to be used by Russian GRU as an operational hub for cyber and political warfare operations, as well as Spetznas infiltration operations and exercises in the area. Airiston Helmihe, an Estonian registered limited corporation, owned the buildings and is believed to be a known front for Russian intelligence services.
Since the dissolution of the Soviet Union, Western democracies have expelled at least 419 Russian spies from SVR, FSB and GRU. That number includes the approximately 180 Russians which were declared persona non grata after the March 2018 attempted murder on Sergei and Julia Skripal in Salisbury, England. In recent years, the majority of those expelled Russian agents have been involved in cyber warfare related operations, including influence, social media tinkering or outright espionage.
The American cybersecurity giant Mitre is one of the companies that has best surveyed the various hacking groups in the world, including groups linked to the intelligence services of various countries. Of the 72 so-called Black Hat-hacker groups on Mitre’s list, 24 originated from China, 6 from Russia, and 9 from Iran. India, Pakistan, North Korea, Vietnam and Lebanon all also featured at least one operative group each which could be affiliated with state actors. The other groups on Mitre’s index are largely criminal groups or so-called White Hat-hackers which merely seek to discover and explore security vulnerabilities.
A problem for cybersecurity researchers in identifying and publishing information about these hacker groups is the perception that the majority of information about state-sponsored cyber activities and affiliated hacking groups comes, not from private investigators or researchers, but from the American intelligence community (USIC). This is largely incorrect. While the USIC has provided a lot of information to its allies and even to the media, it consists of tainted information and usually with large information gaps. The most comprehensive and readily available information on these state-controlled hacking activities tends to come instead from the private sphere. Groups such as FireEye, CrowdStrike, Mitre, F-Secure or Bellingcat are key leaders in this realm.
The term cyber warfare is, in and of itself, quite deceptive. The overall doctrine used to fall under the term Information Warfare which was significantly more telling. This now legacy term implied that it was the management of information, i.e. a new way of creating information bubbles, psychological warfare and propaganda. It is easy to see how crowd-pleasing, commercially enabling information bubbles (also known as filter bubbles) imposed by corporations such as Twitter and Facebook fit under that header.
Control peoples’ information flow and you control their opinions and ability to express themselves. Just look at BREXIT — a very real result, with long-lasting ramifications due to a filter bubble.
Because of the nature of our contemporary interconnected society, it has never been more important – and in our pro-democracy foundation’s best interest – to combat such nefarious attacks on our information infrastructure. Cyber attacks will only increase in the foreseeable future. As such, the fight against hostile cyber acts, be it perpetrated by or on behalf of North Korea, Syria or Russia, is on principle something for all the world’s democracies to be concerned with.
John Sjoholm, for LIMA CHARLIE WORLD
[Edited by Anthony A. LoPresti ]
[Subscribe to our newsletter for free and be the first to get Lima Charlie World updates delivered right to your inbox.]
John Sjoholm is Lima Charlie’s Middle East Bureau Chief, Managing Editor, and founder of the consulting firm Erudite Group. A seasoned expert on Middle East and North Africa matters, he has a background in security contracting and has served as a geopolitical advisor to regional leaders. He was educated in religion and languages in Sana’a, Yemen, and Cairo, Egypt, and has lived in the region since 2005, contributing to numerous Western-supported stabilisation projects. He currently resides in Jordan. Follow John on Twitter @JohnSjoholmLC
REFERENCE: [1] Shorrock, Tim (2008). Spies for Hire: The Secret World of Intelligence Outsourcing. Simon and Schuster. p. 221. ISBN 9780743282246.
Lima Charlie World provides global news, featuring insight & analysis by military veterans, intelligence professionals and foreign policy experts Worldwide.
For up-to-date news, please follow us on twitter at @LimaCharlieNews
In case you missed it:




![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-480x384.jpg)
![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01-480x384.png)
![Image Intelligence Community mobilizes for Cyber War with Russia [Lima Charlie News][Photo: Mark Wilson]](https://limacharlienews.com/wp-content/uploads/2018/08/title-asldkfj-480x384.jpg)


![Blossoming Russo-Turkish alliance leaves U.S., NATO behind [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/07/Russia-Turkey-alliance-leaves-U.S.-NATO-behind-480x384.png)

![Image What exactly is the extent of Russia’s influence on North Korea? [Lima Charlie News][Photo: Yuri Kadobnov]](https://limacharlienews.com/wp-content/uploads/2019/05/What-exactly-is-the-extent-of-Russia’s-influence-on-North-Korea-1-e1557115659181-480x384.jpg)
![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-150x100.jpg)
![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01-150x100.png)