While diplomacy is moving forward with Kim Jong-Un, it doesn’t appear that North Korea’s extensive cyber-warfare capabilities are on the negotiating table.
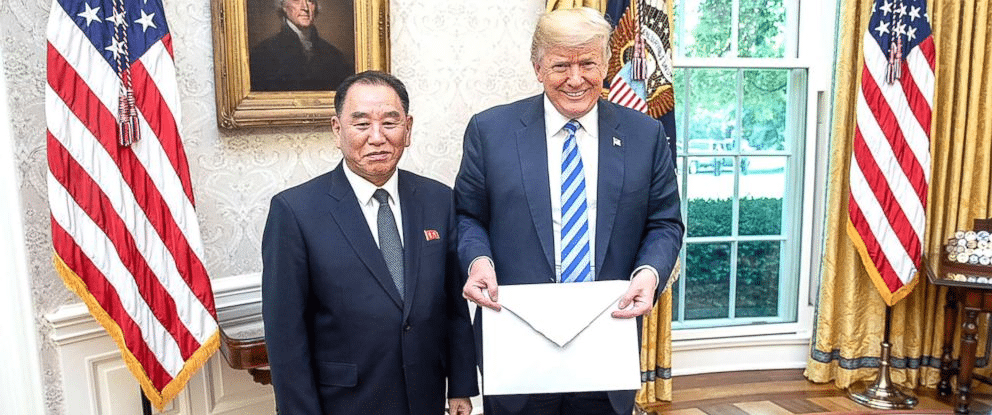
General Kim Yong-Chol, former spy chief of the North Korean intelligence agency, the General Reconnaissance Bureau, played a pivotal role in breaking the diplomatic impasse between North Korea and the U.S. that resulted in last night’s historic summit in Singapore. General Kim had met with President Trump at the White House on June 1st, where he hand-delivered the oversized envelope containing a letter from Kim Jong-Un.
Yet, in order to attend the meeting, and deliver the letter, the general had to be granted a ‘sanctions travel waiver’ having been formally banned from entering the U.S. for his alleged role in a number of noted cyber-attacks on U.S. companies.
The alert identified two families of malware, referred to as Joanap and Brambul, both used by the North Korean government. In a revised version of the alert, issued May 31st, US-Cert provided additional details outlining each of the malware’s capabilities:
Joanap: a two-stage malware used to establish peer-to-peer communications and to manage botnets designed to enable other operations. Joanap malware provides Hidden Cobra actors with the ability to exfiltrate data, drop and run secondary payloads, and initialize proxy communications on a compromised Windows device.
Brambul: a malicious Windows 32-bit Server Message Block (SMB) worm that functions as a service dynamic link library file or a portable executable file often dropped and installed onto victims’ networks by dropper malware. If successful, the application attempts to gain unauthorized access by launching brute-force password attacks. Once the malware establishes unauthorized access, it communicates information to Hidden Cobra actors using malicious email addresses. This information includes the IP address and host name—as well as the username and password—of each victim’s system.
As the alert implies, Hidden Cobra appears connected to other well-known North Korean Advanced Persistent Threat (APT) groups.
IBM’s X-Force Threat Intelligence researchers have indicated that North Korean hackers have been involved in some of the most prolific cyber campaigns including: the breach of Sony Pictures Entertainment (2014), Operation Dark Seoul (2013), Operation 1Mission (2012), 10 Days of Rain (2011), Operation Troy (2009-2012) and Operation Flame (2007-2009). U.S. intelligence also determined that the “Lazarus group,” an elite North Korean hacking unit, was behind the May 2017 WannaCry ransomware attack that infected hundreds of thousands of computers across 150 countries, with total damages ranging from hundreds of millions to billions of dollars. The ransomware cryptoworm demanded ransom payments in Bitcoin, and crippled parts of the UK’s National Health Service.
Some experts believe that North Korea poses a bigger threat of large-scale cyber attacks than Russia. It has long been suspected that North Korea also trains and sends hundreds of hackers abroad to infiltrate and infect corporate servers worldwide. A 2018 CrowdStrike Global Threat report concluded that “DPRK-based adversaries are likely to continue malicious cyber activity against entities in South Korea, Japan and the US” and that “[t]his specific targeting may represent DPRK posturing … that could deliver destructive effects against the US critical infrastructure, should a military conflict occur.”

No Cyber in Singapore
North Korea’s many written promises to cease its nuclear ambitions go back over a quarter of a century. At yesterday’s summit, having declared success, President Trump and Kim Jong-Un signed a document agreeing to a handful of key provisions. A joint statement was issued that read:
“Convinced that the establishment of new U.S.–DPRK relations will contribute to the peace and prosperity of the Korean Peninsula and of the world, and recognizing that mutual confidence building can promote the denuclearization of the Korean Peninsula, President Trump and Chairman Kim Jong Un state the following:
- The United States and the DPRK commit to establish new U.S.–DPRK relations in accordance with the desire of the peoples of the two countries for peace and prosperity.
- The United States and the DPRK will join their efforts to build a lasting and stable peace regime on the Korean Peninsula.
- Reaffirming the April 27, 2018 Panmunjom Declaration, the DPRK commits to work toward complete denuclearization of the Korean Peninsula.
- The United States and the DPRK commit to recovering POW/MIA remains, including the immediate repatriation of those already identified.”
At a news conference after the summit, President Trump stated, “We signed a very comprehensive document and I think he’s going to live up to that.”
In return for Kim’s commitment, Trump announced a freeze on any new U.S. sanctions, and that the U.S. would cease conducting joint military drills with South Korea.
While Kim Jong-Un has signaled a willingness “to work toward” the dismantling of his regime’s nuclear programs, there has been no such indication that he is willing to have a conversation about the regime’s malicious cyber activities. By all accounts, cyber security concerns remain and, at least publicly, have not yet been addressed.
But as President Trump frequently says, “we’ll see what happens.”
LIMA CHARLIE NEWS, by Sean McNicholas, with David Firester and Anthony A. LoPresti
Lima Charlie provides global news, insight & analysis by military veterans and service members Worldwide.
For up-to-date news, please follow us on twitter at @LimaCharlieNews
In case you missed it:

![Image Singapore Summit leaves North Korea cyber threat off the table [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/06/Singapore-Summit-leaves-North-Korea-cyber-threat-off-the-table-Lima-Charlie-News.png)



![Image Intelligence Community mobilizes for Cyber War with Russia [Lima Charlie News][Photo: Mark Wilson]](https://limacharlienews.com/wp-content/uploads/2018/08/title-asldkfj-480x384.jpg)
![Image The Week in U.S. Politics [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/03/Lima-Charlie-Week-in-Politics-01-480x384.jpg)


![Blossoming Russo-Turkish alliance leaves U.S., NATO behind [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/07/Russia-Turkey-alliance-leaves-U.S.-NATO-behind-480x384.png)


![Image Intelligence Community mobilizes for Cyber War with Russia [Lima Charlie News][Photo: Mark Wilson]](https://limacharlienews.com/wp-content/uploads/2018/08/title-asldkfj-150x100.jpg)