A recently released report indicates that the Lebanese General Directorate of General Security (GDGS) operated a special cyberwarfare unit that targeted individuals in over 21 countries. Among the targeted were military and financial institutions in the United States, Canada, the United Kingdom, and Switzerland. The Lebanese intelligence operation is believed to have been active since April 27, 2010, and has likely compromised thousands of individual systems. The breach is likely to have resulted in millions, if not billions worth of private, privileged and sensitive information having been intercepted.

The in-depth report is the result of years of research by a joint task force group consisting of security researchers from mobile security firm Lookout, Inc., and the digital rights group Electronic Frontier Foundation (EFF).
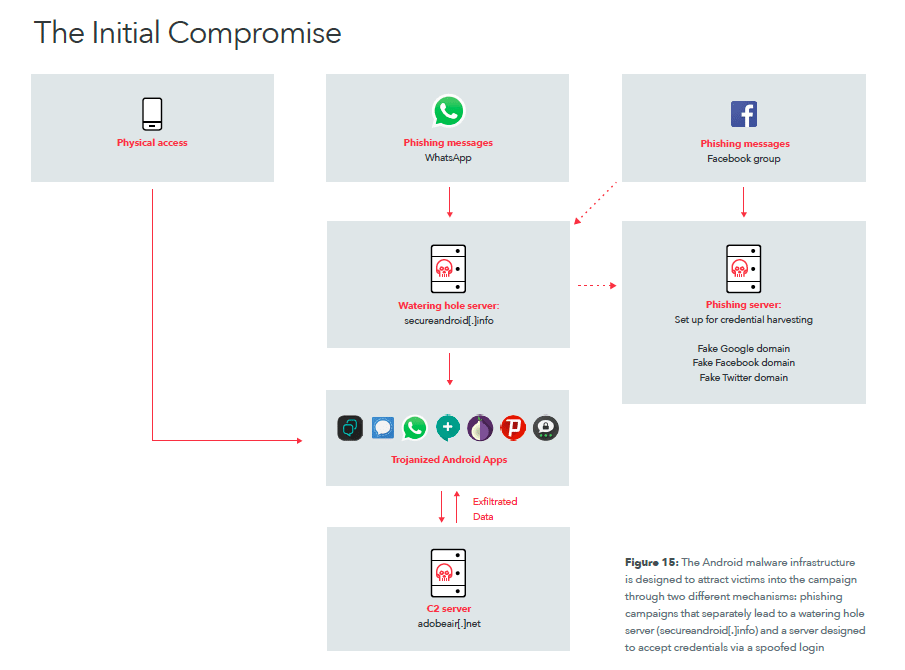
The Lebanese intelligence operation has become known as Dark Caracal, and consisted of at least 11 different Android attack malwares and 26 desktop malwares. The researchers were able to not only show that the intelligence operation captured information from messaging apps such as WhatApp, Telegram, and Signal, on the Google Android smartphone platform, but also that it actively intercepted passwords, voice communication, emails and other account information from the phones. The same technology was also used to breach Windows, Mac, and Linux computers.
Ultimately the information retrieved from the breached smartphones and computers could lead to the Lebanese intelligence agency not just creating a near perfect profile of the individuals, but also breaching other affiliated secure networks.
The biggest puzzle piece came after the researchers discovered a treasure chest of nearly half a terabyte worth of intercepted data stored on a cloud network, which they discovered by tracing where the malicious software was storing its data. The cloud archive is likely the result of a few weeks worth of collected data, and was likely kept there while it was synchronized to other, secure servers inside the GDGS.
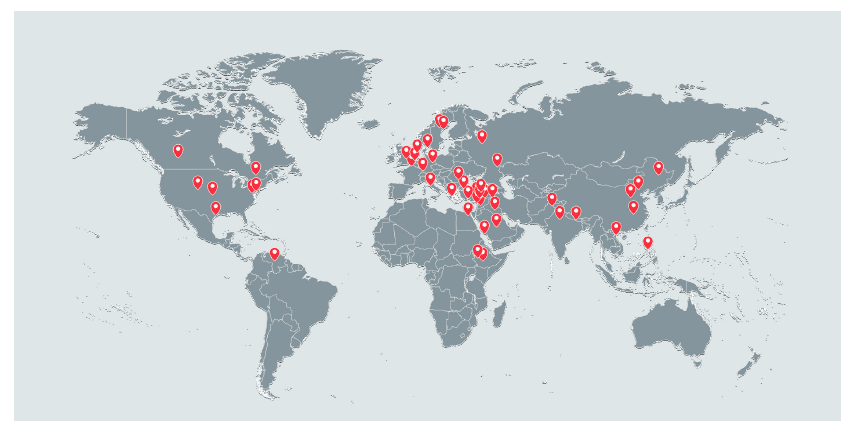
![Image The location of IP addresses that logged into the adobeair[.]net admin console between July and September 2017 (Courtesy of Lookout, Inc. and Electronic Frontier Foundation)](https://limacharlienews.com/wp-content/uploads/2018/01/Dark-Caracal-Lookout-EFF-IP-addresses.png)
By analyzing the data found in the cloud storage system, the researchers quickly discovered that the information retrieval system did not just target Western users, but also Lebanese. The techniques used are eerily similar to Operation Manul, a 2014 operation in Kazakhstan that targeted Kazakh opposition politicians and journalists by covertly collecting information from their smartphones. The Lebanese operation appears to predate the Kazakh government one.
The task force group has released large amounts of its findings, and has notified the authorities in all concerned countries. At present, the group believes it is likely the information retrieval network is operated by at least four individuals. GDGS has yet to make any public comments.
John Sjoholm, Lima Charlie News
John Sjoholm is Lima Charlie’s Middle East Bureau Chief, managing editor, and founder of the consulting firm Erudite Group. A seasoned expert on Middle East and North Africa matters, he has a background in security contracting and has served as a geopolitical advisor to regional leaders. He was educated in religion and languages in Sana’a, Yemen, and Cairo, Egypt, and has lived in the region since 2005, contributing to numerous Western-supported stabilisation projects. He currently resides in Jordan. Follow John on Twitter @JohnSjoholmLC
Lima Charlie World provides global news, featuring insight & analysis by military veterans, intelligence professionals and foreign policy experts Worldwide.
For up-to-date news, please follow us on twitter at @LimaCharlieNews
In case you missed it:



![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-480x384.jpg)
](https://limacharlienews.com/wp-content/uploads/2018/09/Hezbollah-Vehicles-Weapon-Transport-480x384.jpg)
![Image Huawei – China’s telecom giant hits a giant wall [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/01/Huawei-–-China’s-telecom-giant-hits-a-giant-wall-480x384.png)
![Image U.S. 'Space Force' looking more and more like space reality [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/Space-Force-looking-more-and-more-like-space-reality-480x384.png)
![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01-480x384.png)

![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-150x100.jpg)