Part 2 of Capt. Gail Harris’ report about the recent Intelligence & National Security Summit and the challenges facing the Intelligence Community: Cyber Security
The secret is to gang up on the problem, rather than each other.
—Thomas Stallkamp
By Capt. Gail Harris, Lima Charlie News [continued from Part 1].
One of my favorite scenes from the movie Patton, is when General Patton is visited by a British general while fighting German troops in North Africa. Patton had complained earlier to the British, who were in charge of allied air support for that campaign, that the German air force was causing him severe problems. The British didn’t believe him, and had replied to Patton’s concerns with insults. The visiting general again told Patton he was exaggerating, and remarked, “I promise you one thing General, you will see no more German planes.” At that moment German aircraft attacked, as they dove under the table for cover.
I tend to think about that scene as I reflect on my professional journey in the cyber arena. Even though I appreciated the technological advances that made sorting through “Big Data” in order to do intelligence analysis easier, I was still dragged into the computer age kicking and screaming. I would yell to anyone who would listen that computers were evil and temperamental. When asked to speak at computer related conferences and meetings I would usually begin by screaming, “They’re out to get us and will take over the world one day. Remember the Terminator movies!”
I wasn’t being a total jerk. With greater dependence on computers comes greater risk of vulnerabilities, seen and unforeseen. Even as I write this, my hard line internet access just failed, forcing me to my secondary wireless. Go figure….grrrrrr.
But joking aside, my bottom line upfront is this: we are engaged in an undeclared Cyber War and have been for some time. Each year the intelligence community provides an unclassified worldwide threat assessment for Congress. For the last few years cyber has been identified as the number one threat to national security.
Think about that for a moment. Consider all of the effort the U.S. and its coalition allies have put into the fight against terrorism. Consider the concern and level of reporting on other national security issues like Chinese activity in the South China Sea, the resurgence of Russia, and North Korean nuclear activity. With all these very real and tangible threats, the intelligence community still considers cyber to be number one.
Why does that not raise more alarms, or register with the mainstream media and many in the general public? Only recently, news reports of DNC hacking and a planned CIA “Cyber Strike” against Russia have gained some traction, mostly due to perceived interference with our upcoming election.
I think the answer is twofold. First, most of the high profile cyber incidents reported in the mainstream media can be categorized as criminal acts. Admiral Mike Rogers, head of both U.S. Cyber Command and NSA, speaking at the Cambridge Cyber Summit, recently stated, “65% of the total cyber activity of concern that you see out in the Worldwide Web today is largely criminal, groups, individual actors using cyber, using the web as a vehicle to gain access to data which they then turn around for economic advantage.”
Second, most of the really nasty cyber stuff never comes up on the public radar because the government keeps it highly classified. That’s not necessarily a bad thing. Admiral Rogers recently remarked:
In a public forum it can be difficult to explain the nuance and depth of the threats that we at USCYBERCOM see on a daily basis. We must, however, because Congress, the federal government, industry, allies, and the general public should understand the ability and determination of malicious cyber actors. Literally every American who has connected to a network has been affected, directly or indirectly, by cyber crime. By this point millions of us have had personal information stolen, or seen our accounts or credit compromised.
Why is any of this significant?
If you don’t understand the scope of the problem, you can’t come up with a workable solution. Cyber is an issue that cuts across a lot of organizations. Law enforcement, military, business, economic, intelligence community and the public all have roles to play. For instance if a cyber incident is determined to be a criminal act, law enforcement officials address it. The problem is, for example, a bank heist can initially appear to be a criminal act. A subsequent investigation can show, however, that it is in fact part of an attack on multiple banks, by a nation state. This was the case of cyber attacks against U.S. banks widely believed to be attributed to Iran from late 2011 to mid 2013.
We may also be seeing this scenario unfold in the DNC / Wikileaks hacks, which were initially perceived as criminal elements, now believed to be directed by the Russian government. I address this in Part 3 of my series, along with a cautionary tale found in the NATO publication Revolution Hacking, by Nikolay Koval.
In 2014, Koval was Chief of Ukraine’s Computer Emergency Response team. In Revolution Hacking he details how a group named CyberBerkut compromised a Ukrainian election by disabling the software designed to display the vote count in real time. Twelve minutes before the polls closed, the same group posted a picture on the web incorrectly claiming a right wing candidate had won.
If you don’t understand the scope of the problem, you can’t come up with a workable solution.
Laws, regulations, and security procedures continue to lag behind what is needed to address the growing cyber threat. There continues to be a gap in understanding the nature of the threat between those on the frontline – government, the military, private industry dealing with the threat each day – and the general public. Even among those on the frontline, there is no universally agreed upon approach to solving the problem. Instead there is a lot of bickering and lines drawn in the sand over topics like privacy versus national security, encryption, and information sharing.
In the midst of all this, the question is being asked: are we involved in a cyber war, or is it all hype? Phrased another way, could there be a Cyber Pearl Harbor? One of the major lessons learned from the Vietnam war is you can’t win a war, much less solve a problem, without the support of the American public, and all concerned parties.
This is why events like the recent Intelligence & National Security Summit, co-hosted by AFCEA and INSA, and the Cambridge Cyber Summit in Boston, co-hosted by CNBC, the Aspen Institute, and MIT on October 5th are so important. Much of what the government and the military do in the cyber realm is classified. These events provide a venue for senior industry, government, and military officials to interact with, and educate the public about these critical and timely issues – issues that many would rather avoid.
But I wouldn’t even be here today, seeking to educate the public on these issues, if fate hadn’t dragged me into the Cyber Security World of the U.S. Military. Before I go on about key points made during the Summit, I do believe a story is in order.
My introduction to the policy, strategy, and warfare aspects of cyber came at one of the lowest points in my career. One of the things they don’t tell you in school is that the more successful you become, the more likely you are to have to deal with critics. I’ll leave the why of it to Shrinks and Sociologists. I prefer to take the view of Winston Churchill: You have enemies? Good. That means you’ve stood for something sometime in your life.
Shortly after I got promoted to Captain, a rumor surfaced that I was a drunken tramp. Now I was puzzled. Anyone who knows me knows that my favorite drink is Coca Cola, and if 4 or 5 dates a year makes me a tramp…so be it. But as silly as that rumor was, it soon became an issue for the intelligence leadership to find me a job assignment.
I’ve written about it in my book A Woman’s War, but after some trials and tribulations, I was assigned as the initial lead for the intelligence piece of the then new Department of Defense mission: cyber. My task was to work with over 30 Department of Defense commands, and all of the three letter DC intelligence agencies, to develop the role of intelligence. Now I’m aware that one of the reasons I got the job was because most felt it was mission impossible, and apparently no one else wanted it. No one believed you could get the various agencies and departments of the intelligence community to agree on anything because of organizational politics on the issue.
Many in the intelligence community felt there was no role for intelligence types because cyber was a mission for the technical support and communications staff of military commands. I sided with the other school of thought that believed just as the intelligence community tracked the capabilities of potential adversaries to harm us with bombs, missiles, ships, aircraft, etc., we also needed to track their capabilities to harm us with cyber operations.
The command I was assigned to had been given the cyber mission as the initial lead for the Department of Defense a year or so before I arrived. The feeling among many in the intelligence community, who believed cyber was a major new mission, was that nothing had been done and the clock was ticking. I ran into a lot of anger and hostility when I first arrived. I guess some felt I would be useless to help, that because I was not a techno geek, I didn’t understand the issues and would dictate a solution instead of relying on experts and a team approach.
I’m a “bloom where you’re planted” kind of person and ignored all of the negativity. I was very lucky, and was taken under the wing and mentored by three geniuses: Navy Captain Terry Roberts, who was leading an interagency working group that was revolutionizing the way the intelligence community used computers to support military operations; Commander Bob Gourley, who was the first intelligence officer for what would eventually become U.S. Cyber Command; and Don Lewis, a highly decorated Army Veteran who was the lead on Cyber for the Defense Intelligence Agency. I was also very fortunate that Captain Mike Kuhn, my boss, chose to ignore any rumors he’d heard about me and give me a chance. Without his visionary support of my efforts there would have been no progress made. He gave me valuable top cover and course correction as needed.
I mention these folks because they are the unsung heroes of the Cyber War, and although they are well known and respected in the cyber community, more people need to know about them. We held a conference with representatives from the military, intelligence and private industry, and in one week working together as one team, solved problems that people had been working on for two years that had been considered impossible.
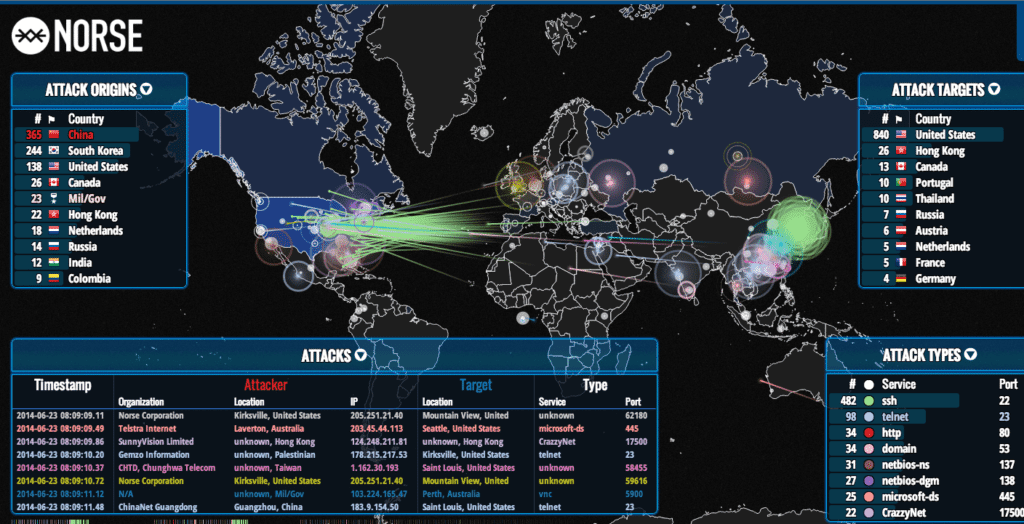
We focused on three areas: under what circumstances would the intelligence community get involved and report on cyber incidents, as opposed to the technical and communications staffs of organizations or law enforcement; sharing information on cyber incidents through using the same or interoperable data bases; and deciding what type of information the intelligence community needed to collect to be able to do analysis of cyber incidents, and to perform indications and warnings of cyber threats.
I retired from the Navy about a year later, and my direct involvement in the cyber arena ended. Don Lewis has said he’s been asked at many conferences to tell the story of how we were able to get so many people and organizations to agree and work together, to solve critical problems in just a week. There were two reasons; first we all came to agreement on the actual nature of the problem. As I’ve stressed many times, if you don’t fully understand the problem, you can’t come up with the right solutions. Second, we remembered who we were there to support: the war fighter and the nation. Our effort can best be summed up with the slogan:
One Team, One Fight.
For me the story of our accomplishment is critical because many of the same issues we’re debating today, like privacy, information sharing, concerns about the intelligence community spying on U.S. citizens, the need for a partnership between industry and the government, etc., were being discussed then. The scene from the Patton movie also comes to mind because I think the cyber story can be told as a continuous attempt to inform and educate the skeptics about a very real threat, and the need to identify solutions.
All of my colleagues involved in that effort became missionaries preaching to senior members of the Defense and Intelligence communities about the Hell we’d be facing if we didn’t come up with solutions to potential dangers caused by Cyber. For example, Jason Healey, who was working for Bob Gourley when I met him, has continued his great work. In his book A Fierce Domain: Conflict in Cyberspace 1986 to 2012, I think he best describes the threat environment we were dealing with. He wrote:
For over twenty-five years, nation states and non-state groups have been using computer networks to strike, spy upon, or confound their adversaries. While many of these dust ups have been mere nuisances-more playground pranks than real battles, several incidents have become national security issues, which have placed militaries on alert and prompted warnings to heads of state, the US President included.
Indeed, we’ve long crossed the threshold from mere nuisances and playground pranks. We now face very real national security threats, including the threat of Cyber War.
But I leave further discussion about that threat, and lessons learned from the Intelligence & National Security Summit, for my next installment. As always, my views are my own.
Gail Harris, Lima Charlie News
Captain Gail Harris (U.S. Navy, Ret.), was the highest-ranking African American female officer in the US Navy at the time of her retirement in 2001. Her 28 year career in intelligence included hands-on leadership during every major conflict from the Cold War, to El Salvador, to Desert Storm, to Kosovo, and she was at the forefront of one of the Department of Defense’s newest challenges, Cyber Warfare. Gail also writes for the Foreign Policy Association, is author of “A Woman’s War”, serves as Senior Fellow for the George Washington Center For Cyber & Homeland Security and is a Senior Advisor for the Truman National Security Project.
Lima Charlie World provides global news, featuring insight & analysis by military veterans, intelligence professionals and foreign policy experts Worldwide.
For up-to-date news, please follow us on twitter at @LimaCharlieNews







![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-480x384.jpg)
![Image Huawei – China’s telecom giant hits a giant wall [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/01/Huawei-–-China’s-telecom-giant-hits-a-giant-wall-480x384.png)
![Image U.S. 'Space Force' looking more and more like space reality [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/Space-Force-looking-more-and-more-like-space-reality-480x384.png)
![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01-480x384.png)

