Capt. Gail Harris, Lima Charlie News Senior Correspondent for Cyber & Homeland Security, reports on the recent DDoS attack of Dyn, Inc. that took down a big chunk of the Internet, and how we may be in the midst of a Cyber War.
Imagine an adversary exploiting a flaw in your home lawn sprinkler and from there leaping into your toaster and then your watch to steal your work login and then leaping into your office computer…This might sound like a bad science fiction movie, but the trends of technology and lessons of history say this is the world of the near future.
— Bob Gourley, The Cyber Threat
By Capt. Gail Harris, Lima Charlie News
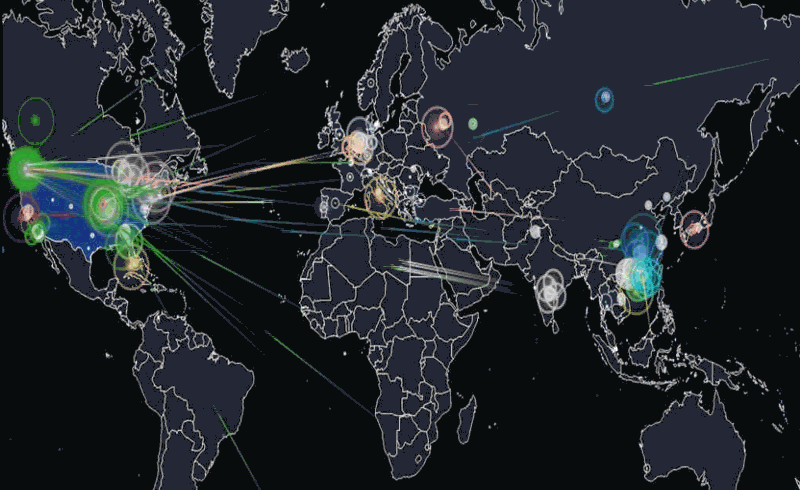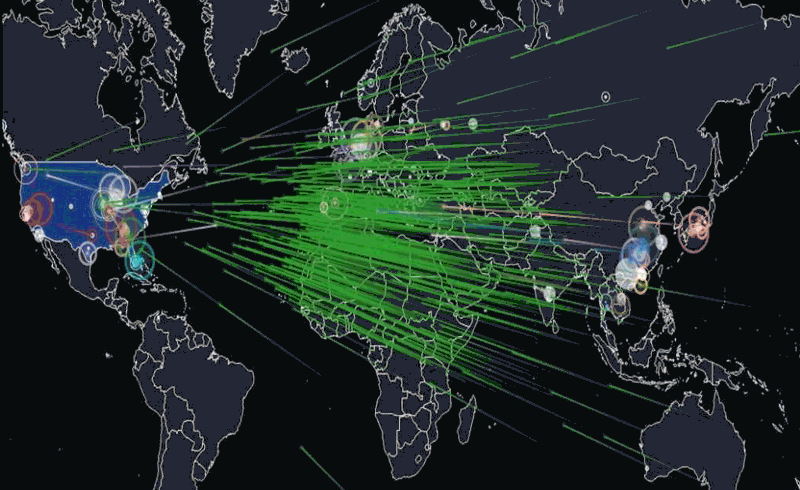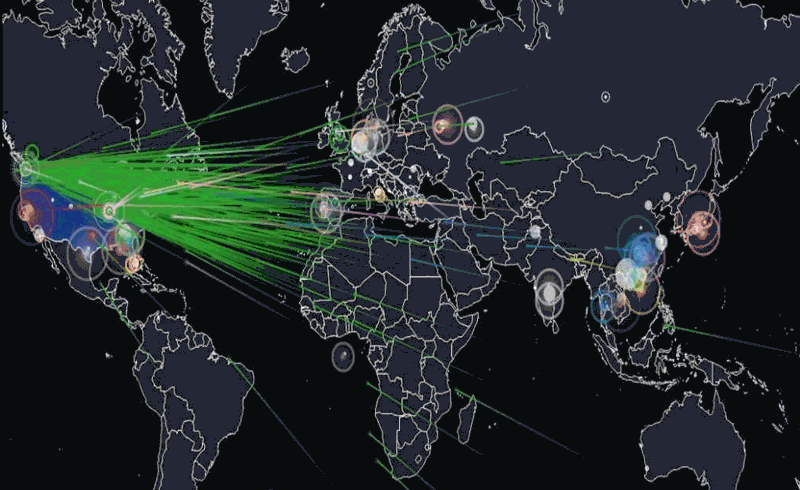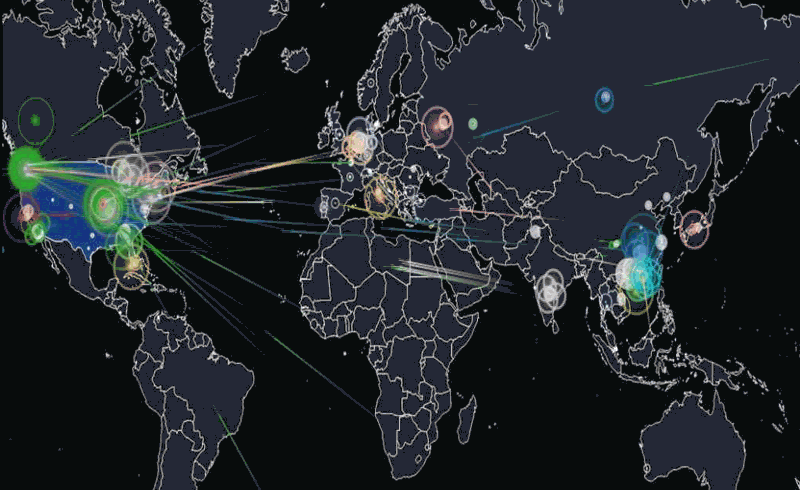
Friday morning, October 21, 7:10 a.m. EST: Dyn, Inc., a New Hampshire internet company, experienced a massive distributed denial-of-service (DDoS) attack against its Domain Name System (DNS) infrastructure. Dyn would experience three waves of attacks before the situation was resolved 11 hours later. In that time, dozens of major websites, first on the East Coast, later throughout the country, including Twitter, Amazon, The New York Times, Spotify, Reddit, Airbnb and Netflix would find their services slowed or knocked offline. Dyn would later describe the events as a “sophisticated, highly distributed attack involving 10s of millions of IP addresses.” Speculation as to how and where the attack came from abounds. Was it a Russian based attack? Chinese? North Korean? Terrorists? A lone wolf?
A DDoS attack is an attempt to take down an online service or website by overwhelming it with a large amount of traffic, until it collapses under the load, interrupting its service. According to one source there are over 2000 such attacks observed daily. [For a tutorial on DoS attacks: guru99.com].
I reached out to Bob Gourley, a partner in Cognito Corp and one of the pioneers in Cyber security for his take on the situation. Gourley said, “Overall there has been a 75% increase in DDoS attacks over this time last year, and peak attack size is now at the astronomical size with about a third of the attacks being over 10 Gbps, which will swamp most all. The largest attacks in recent history have been over 600 Gbps.”
What else made the DDoS attack against Dyn significant? There were a couple of things. First instead of attacking a web site, the attack was against the company’s DNS infrastructure, which then caused clients the company supports to suffer major problems with their web sites. In military terms, it’s like where can I drop a bomb to do the most damage? They got a greater bang for the buck by hitting the DNS infrastructure.
What does a DNS infrastructure do? Humans can contact each other on the telephone by dialing a number that’s unique to whoever you want to call. Computers identify each other through Internet Protocol Addresses (IP). They too consist of a group of numbers. Because of the wonders of a DNS infrastructure provided by companies like Dyn, you just type in nsa.gov and it automatically converts it to an IP address and then routes it via the most efficient pathway to the requested website. An easier way of thinking of this is a description Gourley passed on: “DNS is the switchboard connecting computers and domain names.
A second thing that makes this incident significant is that the method of attack was different than most others. Normally, the attackers use groups of computers called botnets that have been infected with malware through emails, web sites, etc., which allow them to be controlled remotely to launch the attack. Most times owners of the devices are not aware their computers have embarked on a life of crime. Dyn’s Chief Strategy Officer Kyle York said:
This particular attack was due to open source malware called the Mirai Botnet. It basically goes and infects things in your home, think like your thermostat, DVR, smart phone or web cam.
York said they were hit with tens of millions of IP addresses from around the world. He remarked that it was difficult to figure out where the virus came from. York also said they are working with Federal agencies on ways to improve security.
Some may say, “Okay Gail, Dyn successfully fought off all of those botnet things so what is the problem?”
This is the beginning of a new phase in what I’ve been calling an undeclared Cyber War, and that is the impact of not having addressed the security implications of the Internet of Things (IoT). That’s the buzzword for all of these new smart devices hitting the mainstream that are connected to the internet by wireless communications. Cyber security specialists have long been sounding the alarm that although there are many benefits to smart devices, if you don’t have security systems in place, you’re looking at major problems. Anything that is connected to the internet can fall victim to a cyber attack and is also in danger of becoming a bot.
The challenge with IoT smart devices is that even if they’re being used as bots, you probably won’t know it. Apparently they continue to do their “normal” job.
A year or so ago, my refrigerator broke down. Since it was fairly new I was highly irritated. The repair guys fixed it. I asked what the problem was, and they said the thing’s computer had died. I didn’t even know it had a computer. Now, each day I look at it and wonder if it’s been involved in criminal activity overnight.
I attend a lot of forums and conferences on computer topics. There is a general consensus that the number of smart devices connected to the internet will greatly increase. Some estimates go as high as 50 billion devices by 2020. We’re not just talking about things like home security systems, security cameras, DVRs, but also things like toasters and even toilets and tooth brushes being hooked up to the internet. I have visions of getting a concerned call from my doctor because my toilet sent her an email warning of high blood sugar based on its analysis of my bodily fluids that morning. Yuck. This security problem is only going to get worse if we don’t start to address it now.
Gourley says, “These bots are working by automatically guessing passwords and then reconfiguring IoT devices like cameras. The easiest passwords to guess are those that have not been changed from factory settings. So one thing all of us can do to help prevent this attack is change all default passwords on all devices.”
Last month I read a blog by Bruce Schneier titled, Someone Is Learning How to Take Down the Internet. He stated:
Over the past year or two, someone has been probing the defenses of the companies that run critical pieces of the Internet. These probes take the form of precisely calibrated attacks designed to determine exactly how well these companies can defend themselves, and what would be required to take them down. We don’t know who is doing this, but it feels like a large nation state. China or Russia would be my first guesses.
He also remarked:
Recently, some of the major companies that provide the basic infrastructure that makes the Internet work have seen an increase in DDoS attacks against them. Moreover, they have seen a certain profile of attacks. These attacks are significantly larger than the ones they’re used to seeing. They last longer. They’re more sophisticated. And they look like probing. One week, the attack would start at a particular level of attack and slowly ramp up before stopping. The next week, it would start at that higher point and continue. And so on, along those lines, as if the attacker were looking for the exact point of failure.
I’ve been writing for quite some time that I believe we are in an undeclared Cyber War. Critics have told me that the majority of cyber attacks are criminal in nature. In my last article I mentioned that Admiral Rogers, the head of both U.S. Cyber Command and NSA, said that about 65% of what they see is in the criminal realm. But I would submit that argument can be made, what initially may be perceived as a criminal act, is instead the activities of a nation state or terrorist group.
Each day I look at my refrigerator and wonder if it’s been involved in criminal activity overnight.
During a press conference on Friday, White House Press Secretary Josh Earnest was asked about the Dyn attack. He replied:
I have seen the reports of this. I know that the Department of Homeland Security — that is the U.S. government agency that is responsible for monitoring our security in cyberspace and coordinating with the public and private sector to protect U.S. interests in cyberspace — is monitoring this situation. And they’ll take a close look at it. But at this point, I don’t have any information to share about who may be responsible for that malicious activity.
I know there is a lot of analysis being done right now, but it would not surprise me if Russia was behind this. This is purely speculation on my part, but it seems odd that this would happen right after the U.S. officially “named and shamed” them as being responsible for the DNC hacks and the probing of a number of state electoral systems.
Last week Vice President Joe Biden stated that we will respond to these hacks by the Russians in a time and method of our choosing. Could this Dyn situation be a shot across the bow fired by the Russians in response to his statements? As I mentioned, this is purely speculation on my part, but I will watch with interest as the investigations continue.
That said, I also wondered after initial reports that Russia was the probable culprit of the DNC hacks and a number of state electoral systems, if we figured that out because we were smarter, or did they let us detect them on purpose? They don’t have to actually try to affect the election outcome through hacks. They’ve already caused a lot of fear and anger from many who wonder if the elections will be “rigged”.
I reached out to Bob Gourley for this article because he is far more knowledgeable than I on this topic. In his book, The Cyber Threat, he points out that most agree cyber attacks come from the following groups: nation states, organized crime and industrial spies, terrorist and other extremist groups, hackers and hacktivists, and trusted insiders. It will be interesting to see how this plays out and what category the Dyn attackers fall under.
As for this attack, he states, “I only have speculation and circumstantial evidence, but this could be a lone wolf attacker using bot-net software that has been made open source and easy to modify.” I have no doubt that the people working this issue in the government are looking at all angles.
The other thing that comes to mind for me as I reflect on the Dyn hack, is that shutting down all or part of the internet with cyber attacks can turn into a national security issue. The target may appear to be a civilian business or organization, but depending on the circumstances, it could have a negative impact on our critical infrastructure and/or our national security apparatus.
Additionally, the Department of Defense is constantly dealing with cyber “incidents”. It’s hard to get exact figures because those are usually classified, but every now and then you can get some sense of the size of the problem. In February 2014, then Secretary of Defense Chuck Hagel, speaking at the retirement ceremony of General Keith Alexander, stated:
During the course of my remarks today, DOD’s systems will have been scanned by adversaries around 50,000 times.
Some say most of this activity would fall under the category of espionage. I’ve long felt that a good part of these incidents would fall under what military types call “intelligence preparation of the battlefield.” Basically, figuring out where our strong and weak points are in our computer network defense. Traditional espionage targets are things like weapons capabilities, war plans, and tactics, techniques and procedures. My concern is that in this new environment, potential adversaries are looking for ways to make things fail at a time of their choosing. The military is heavily dependent on communications. You have to retain connectivity to get the critical information needed to conduct military operations. Adversaries know that cyber is a lifeline for the military.
In terms of warfare, cyber is many things. It’s a weapon and it’s a domain that military forces operate in. Critics accuse the DoD of militarizing the internet, but they are missing two major points. Since the military is heavily dependent on cyberspace for its day-to-day operations, if there is a problem, regardless of what group, individual, or nation state caused it, they along with many in business and the public could be impacted negatively. For example, when I first became involved in cyber in 1999, about 90 percent of military communications went over a commercially owned circuit at some point in their transmission. A 2008 report by the Defense Science Board stated: “About 85% of the energy infrastructure upon which DoD depends is commercially owned, and 99% of the electrical energy DoD installations consume originates outside the fence.” 95% of all internet traffic travels under the sea.
What do we need to do to prevent even greater and more complex cyber attacks? I asked Terry Roberts, Founder & President of Whitehawk, Inc., one of the most respected voices in the cyber arena that very question. She replied:
This particular attack leverages standard DDOS and BotNet threat vectors but its impact was skillfully magnified via IOT.
Frankly I am fed up by our inability to harness more effectively all the disparate cyber related research, analytics and sharing efforts across government, industry and academia – as we did at the onset of the nuclear age.
This could be expeditiously accomplished by focusing government and industry Cyber R&D investments and aligning a partnership across three to four well resourced, university based Cyber Institutes (MIT Lincoln Lab, Hopkins APL, CMU CERT – to name a few). Without comprehensive, collaborative, and well resourced centers of mass that all can work with and contribute too – we will continue to be behind, react to and be done to – by a growing number of cyber criminals. Enough.
Bob Gourley advised:
Organizations can do other things, like using smarter ways of filtering traffic. The networking community has reached broad agreement on how to do this and published best practices on this well known approach, called Best Community Practice (BCP) 38. That will help stop DDoS attacks. In this particular attack, a provider of DNS services was hit. DNS is the switchboard connecting computers and domain names. There are many professional providers of DNS services. We recommend picking a DNS provider based on their ability to sustain the biggest attacks. Pick someone who invests with the intent of being able to weather the storm and keep their clients up. For example, Verisign. They run the .com and .net and .gov DNS infrastructures and have gone 18 years with no outage.
I couldn’t agree more. As always my thoughts and opinions are my own.
[Editor’s Note: Capt. Harris’ analysis has proven correct in that as of the time of this publication, a Chinese electronics manufacturer has announced that its DVRs and internet connected cameras were infected by Mirai malware, inadvertently aiding the Dyn hack.]
Gail Harris, Lima Charlie News
Captain Gail Harris (U.S. Navy, Ret.), was the highest-ranking African American female officer in the US Navy at the time of her retirement in 2001. Her 28 year career in intelligence included hands-on leadership during every major conflict from the Cold War, to El Salvador, to Desert Storm, to Kosovo, and she was at the forefront of one of the Department of Defense’s newest challenges, Cyber Warfare. Gail also writes for the Foreign Policy Association, is author of “A Woman’s War”, serves as Senior Fellow for the George Washington Center For Cyber & Homeland Security and is a Senior Advisor for the Truman National Security Project.
Lima Charlie provides global news, insight & analysis by military veterans and service members Worldwide.
For up-to-date news, please follow us on twitter at @LimaCharlieNews
For a tutorial on DoS attacks, visit guru99.com




![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-480x384.jpg)

![Image Huawei – China’s telecom giant hits a giant wall [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/01/Huawei-–-China’s-telecom-giant-hits-a-giant-wall-480x384.png)
![Image U.S. 'Space Force' looking more and more like space reality [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/Space-Force-looking-more-and-more-like-space-reality-480x384.png)
![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01-480x384.png)

![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-150x100.jpg)