Opinion: Capt. Gail Harris reports on cyber warfare and Russia’s malign influence operations. Where are we and where do we still need to go?
One of my favorite quotes is one the Reverend Martin Luther King, Jr. liked to use from the words of an old minister: “Lord we ain’t what we should be and we ain’t what we gonna be, but thank God, we ain’t what we was!”
That quote was foremost in my mind as I drove out to Aspen, Colorado to attend this year’s Aspen Security Forum. I was eager to hear what advances have or have not been made in addressing the top national security threat of our time: cyber warfare.
Attending events like this allows me to get updated directly from the people currently leading the charge. I’ll talk more about what I see as the desired end state shortly.
Each year the intelligence community provides Congress with a Worldwide Threat Assessment. Since 2013, the cyber threat has been at the top of the list. An unclassified version of the 2018 report is available online and can be accessed here.
I’ve written about it before, but my last active duty assignment was working as the military intelligence lead for developing and determining what role, if any, the intelligence community would play in cyber. It involved working with over 30 Department of Defense commands and all the three letter intelligence agencies in Washington. It was one of the most challenging but ultimately most satisfying things I’ve ever done.
All of the issues being talked about today were being discussed and debated then; privacy, information sharing, etc. Because of the hard work and dedication of many unsung heroes, we’ve come very far, but we still have a long way to go. I believe it will take a 9/11 type event to get everyone out of their silos of self-interest and on the same sheet of music to pass laws and regulations needed.
“Anybody who thinks that Vladimir Putin doesn’t have his stamp on everything that happens in Russia is misinformed. It is very clear that virtually nothing happens there of any kind of consequence that Vladimir Putin doesn’t know about or hasn’t ordered” —DNI Coats #AspenSecurity pic.twitter.com/AOZTX0H97t
— Aspen Security Forum (@AspenSecurity) July 19, 2018
On July 13th, Director of National Intelligence (DNI), Dan Coats spoke before the Hudson Institute, a D.C.-based think tank, to emphasize that the lights are indeed blinking red:
“You only need to go back less than two decades ago to put, I think, the current cyber threat into its proper context. In 2001, our vulnerability was heightened because of the stovepipe approach of our intelligence and law enforcement communities that produced what they called “silos of information.” At the time, intelligence and law enforcement communities were identifying alarming activities that suggested that an attack was potentially coming to the United States. It was in the months prior to September 2001 when, according to then CIA Director George Tenet, the system was blinking red. And here we are nearly two decades later, and I’m here to say the warning lights are blinking red again. Today, the digital infrastructure that serves this country is literally under attack.”
Last week, an impressive group of the leaders of every major intelligence agency in the U.S. addressed the nation at a press conference to emphasize the ongoing threat of Russian cyber attacks and malign activities against the U.S. and its allies, and to reassure the public that every effort was being made to protect the coming midterm elections.
DNI Dan Coats was joined by FBI Director Christopher A. Wray, National Security Adviser John R. Bolton, National Security Agency head Gen. Paul M. Nakasone, and Secretary of Homeland Security Kirstjen Nielsen, to stress to the nation that the Russia cyber threat was indeed not a hoax.
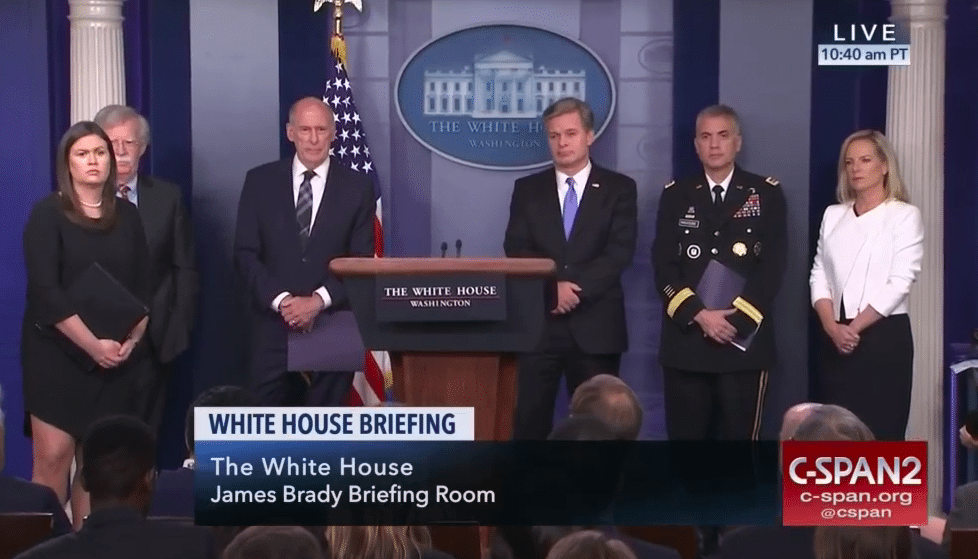
“Russia attempted to interfere with the last election and continues to engage in malign influence operations to this day. This is a threat we need to take extremely seriously and to tackle and respond to with fierce determination and focus,” said Director Wray.
Secretary of Homeland Security Kirstjen Nielsen added, “Our democracy itself is in the crosshairs. Free and fair elections are the cornerstone of our democracy, and it has become clear that they are the target of our adversaries, who seek, as the DNI just said, to sow discord and undermine our way of life. I fully share the intelligence community and the ODNI’s assessments of past efforts and those today to interfere with our election and of the current threat. Our adversaries have shown they have the willingness and capability to interfere in our elections.”
[Full video, courtesy CSPAN][Full Transcript here]
As would be expected, Russian interference in the 2016 election was a frequent topic of conversation during the Aspen conference. A big takeaway for me was that although the intelligence community is seeing signs of Russian interference in the 2018 midterm elections, so far cyber activity is not on the level seen in 2016. This was repeated at last week’s press conference.
In Aspen, DHS Secretary Nielsen said, “Their intent is absolutely to interfere in our democracy… It’s July. We still have August, we still have September, we still have October. We have November. I think we should be absolutely prepared to assume that they will try to interfere in all 50 states.”
FBI Director Christopher Wray reinforced this outlook. “We haven’t yet seen an effort to target specific election infrastructure this time, but certainly other efforts, what I would call malign influence operations, are very active. We could be just a moment away from it going to the next level. So to me, it’s a threat that we need to take extremely seriously and respond to with fierce determination and focus.”
Director Wray, at last week’s press conference clarified the threat further.
“So just a few examples of some of the things we’ve seen over the past: targeting U.S. officials and other U.S. persons through traditional intelligence tradecraft; criminal efforts to suppress voting and provide illegal campaign financing; cyberattacks against voting infrastructure, along with computer intrusions targeting elected officials and others; and a whole slew of other kinds of influence, like both overtly and covertly manipulating news stories, spreading disinformation, leveraging economic resources, and escalating divisive issues.”
What about our election infrastructure?
I found recent comments made by DNI Dan Coats in D.C. at the Hudson Institute very compelling. He remarked, “we fully realize that we are just one click of the keyboard away from a similar situation repeating itself … we are seeing aggressive attempts to manipulate social media and to spread propaganda focused on hot-button issues that are intended to exacerbate socio-political divisions.” Coats added, “Despite public statements by the Kremlin to the contrary, we continue to see individuals affiliated with the St. Petersburg-based Internet Research Agency creating new social media accounts, masquerading as Americans, and then using these accounts to draw attention to divisive issues.”
DNI Coats also mentioned the recent indictment of 12 Russian military intelligence officials related to the 2016 election. Coats also put things into perspective saying:
“But focusing on the potential impact of these actions on our midterm elections misses the more important point: these actions are persistent, they are pervasive, and they are meant to undermine America’s democracy on a daily basis, regardless of whether it is election time or not. Russian actors and others are exploring vulnerabilities in our critical infrastructure as well. The DHS and FBI — in coordination with international partners — have detected Russian government actors targeting government and businesses in the energy, nuclear, water, aviation and critical manufacturing sectors.”

“We do see a concerning increase in country’s nation-state attempts to infiltrate our critical infrastructure. We’ve issued a series of products specific to Russia attempting to intrude into our critical systems, energy systems, aviation, and others,” Manfra said. “On the positive side … private sector and government work very well together, and we were able to stop them from achieving any of their goals.”
Ms Manfra stressed that “We also don’t have perfect visibility into our critical infrastructure. Most of them are owned by the private sector … So we need to work with the private sector to understand what they see, so that we can correlate and better understand Russia, or any nationstate that’s seeking to infiltrate our critical infrastructure.”
Kim Wyman, Secretary of State for Washington State, speaking in Aspen made very interesting points that bought some clarity to a question that had been bothering me. The federal government reported that Russia had attempted to infiltrate the electoral systems of 21 states. Yet, according to reports I’d seen, the affected states were not notified until over a year later. I felt if that were indeed true then heads needed to roll.
First, Ms Wyman pointed out that for some it may seem that cybersecurity is new to elections, but she said they’d been in that field for the last 15 – 20 years. She remembered her concern when she watched Assistant Secretary Manfra being interviewed by Congress saying that Russia had indeed attempted to hack into the systems of 21 states. That was the first time she’d heard of it, and when she asked if her state was one of the 21 the response was, “Well, we can’t tell you.” Ms Wyman said it was rough dealing with the federal government for a few months, but once she understood the “why” she was okay. The why is they were still working through the intelligence and making sure to not release classified information.
Manfra said they did notify the “victim” but apparently didn’t at the time know they needed to also notify the relevant Secretaries of State:
“Where we ran into some issues that we didn’t fully appreciate at the time, is even though we notified the targets, or the potential victims, we didn’t, at the same time, have that sort of communications mechanisms with the Secretaries of State … We recognized that it was important to go back and talk to all the actual heads of the election communities in those states, to walk them through what actually happened.” Manfra added, “There’s a lot of sort of reporting out there that we didn’t notify until a year after it happened. That’s not true. We did notify the actual targets. What we did a year later was actually engage with all the election senior administrators … now we have in place a protocol so it’s very clear who DHS is going to notify in the event that there’s anything happening within their state.”
While that explanation made me feel somewhat better, I believe they should have set up early on who needed to be notified within an organization when cyber incidents occur. Also needed is a clear process for sanitizing cyber incidents so information can be passed to as large an audience as necessary, and to ensure that those who need a security clearance to do their job have one.
The Naval Intelligence community did a lot of work in this area during the Cold War. If you can’t get information to the people who need it in time and in an understandable format then what good is it? More importantly what good are you? Generally speaking, information is classified because of the sources and methods used to obtain it. We developed procedures for getting the information out at the lowest classification level possible without revealing sources and methods behind it.
Now this is not the end. It is not even the beginning of the end.
But it is, perhaps, the end of the beginning.
-Winston Churchill
Are we there yet?
I’ll conclude by giving my two cents on what needs to be done to improve our cyber warning response. Before I do, I’d like to remind folks that cyber threats are certainly not a new problem. As Jason Healey says in his outstanding book A Fierce Domain: Conflict in Cyberspace 1986 to 2012: “For over twenty-five years, nation states and non-state groups have been using computer networks to strike, spy upon, or confound their adversaries. While many of these dust-ups have been mere nuisances-more playground pranks than real battles, several incidents have become national security issues, which have placed militaries on alert and prompted warnings to the President.” Starting with the Clinton administration, each new President has applied more and more effort as the threat increased. This is not a partisan problem.
Well Hello, we’re already at war on the Cyber front with Russia. The problem is there’s still no universally accepted definition of what constitutes a cyber act of war or even what is a cyber attack https://t.co/2dScRdMNGl
— Capt. Gail Harris (@GailHarrisLC) July 19, 2018
First off we need to work with our allies to develop an agreed upon cyber lexicon. As I’ve written many times, there are still no universally agreed upon definitions of what constitutes a cyber attack, a cyber act of war, etc. Does this include malign influence operations via social media, for example.
NATO has done a lot of work in this area and is perhaps best positioned to lead the charge on this. NATO’s Cooperative Cyber Defence Centre of Excellence states that it is “a multinational and interdisciplinary hub of cyber defence expertise. The Tallinn-based international military organization focuses on technology, strategy, operations and law.”
Mikk Marron @MarrMikk, Director General, Estonian Foreign Intelligence Service responding to question on Russian activities: “We shouldn't continue to practice figure skating when the other team is playing hockey". #AspenSecurity pic.twitter.com/3w0u4UlC1P
— Capt. Gail Harris (@GailHarrisLC) July 20, 2018
Second, an enemy or potential enemy has to know what the red line is, and if they cross that line, they will get a response. Now I’m not talking about the diplomatic equivalent of sitting on a chair in a corner by themselves for a time out.
Third, we have got to continue to work on better information sharing between government and industry. Private industry owns 90% of our critical infrastructure. The government can’t protect you if they don’t know what’s happening on your networks.
I asked Kirstjen Nielsen about this and she said it was an area they were working on and seeing improvement. On July 31st she hosted a conference in New York City with industry on this topic. I’m much encouraged by these developments. The conference showed some very positive moves for the way forward. Secretary Nielson announced that the Department of Homeland Security was launching the National Risk Management Center. According to Ms Nielson the new organization housed at DHS will “bring together government experts with willing industry partners so that they can influence how we support them” and the goal is “to simplify the process—to provide a single point of access to the full range of government activities to defend against cyber threats.” Secretary Nielson added, “I occasionally still hear of companies and locals that call 9-1-1 when they believe they’ve been under a cyberattack, the best thing to do would be to call this center.”
During the 31 July event, Secretary Nielson’s keynote comments were one of the best rundowns on the cyber threat that I’ve seen lately. Her remarks can be accessed here.
I highly recommend you take the time to read them.
I asked @SecNielsen how well cyber incident sharing was going between @DHSgov & private industry: “Improving” citing #CyberSummit. Most critical infrastructure is in the hands of private industry. Fmr NSA/CYBERCOM Adm. Rogers famously said he can't defend networks he can't see
— Capt. Gail Harris (@GailHarrisLC) July 19, 2018
A second thing that gave me hope was the announcement during the Aspen conference by Rod Rosenstein, Deputy Attorney General for the Justice Department, of the publishing of a report by the AG’s Cyber-Digital Task Force. Rosenstein said, “The report addresses a wide range of issues including how to define the multi-faceted challenges of cyber-enabled crime, how to develop strategies to detect, deter, and disrupt them; how to inform victims in the public about the threats they face, and how to maintain a skilled workforce to detect and to respond to cyber threats.”
Rosenstein’s Aspen comments can be accessed here.
These are just more beginning steps for confronting cyber warfare and far more will be needed.
Winston Churchill said it far more eloquently than I ever could: “Now this is not the end. It is not even the beginning of the end. But it is, perhaps, the end of the beginning.”
When I first took on this issue nearly 20 years ago (gasp!) I knew it was an enormous problem and that solving it would not just involve a whole of government, industry, and civilian agencies approach but it would involve working and cooperating with our international partners as well. I used the old saying, how do you eat an elephant? One bite at a time.
The bad guys and girls are just scratching the service of the havoc they can bring about. Technology is changing at the speed of thought and the rules and regulations dealing with it are moving at the speed of a glacier.
Think I’ll end here.
Gail Harris, Lima Charlie News
[Edited by Anthony A. LoPresti]
Captain Gail Harris (U.S. Navy, Ret.), was the highest-ranking African American female officer in the US Navy at the time of her retirement in 2001. Her 28 year career in intelligence included hands-on leadership during every major conflict from the Cold War, to El Salvador, to Desert Storm, to Kosovo, and she was at the forefront of one of the Department of Defense’s newest challenges, Cyber Warfare. Gail also writes for the Foreign Policy Association, is author of “A Woman’s War”, served as Senior Fellow for the George Washington Center For Cyber & Homeland Security (2015-2017) and is a Senior Advisor for the Truman National Security Project.
Follow Capt. Harris on Twitter @GailHarrisLC
Lima Charlie World provides global news, featuring insight & analysis by military veterans, intelligence professionals and foreign policy experts Worldwide.
For up-to-date news, please follow us on twitter at @LimaCharlieNews
In case you missed it:

![Image GailForce: Blinking Red - Cyber War and Malign Influence Operations Today [Lima Charlie News][Graphic: Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/GailForce-Blinking-Red-Cyber-War-and-Malign-Influence-Operations-Today-Lima-Charlie-News-01.png)


![Image GailForce to Space Force: 'Make it so' - the Space Force debate continues [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Space-Force-01-480x384.png)
![Image Intelligence Community mobilizes for Cyber War with Russia [Lima Charlie News][Photo: Mark Wilson]](https://limacharlienews.com/wp-content/uploads/2018/08/title-asldkfj-480x384.jpg)
![Israel-Hamas Cyberwar, when old warfare meets new [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Israel-Hamas-cyber-warfare-01-e1558501438770-480x384.jpg)
![Image Huawei – China’s telecom giant hits a giant wall [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/01/Huawei-–-China’s-telecom-giant-hits-a-giant-wall-480x384.png)
![Image U.S. 'Space Force' looking more and more like space reality [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/08/Space-Force-looking-more-and-more-like-space-reality-480x384.png)
![Image #GailForce: U.S. Intelligence community confirms ongoing Russian 'malign influence' operations at Aspen Security Forum [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2018/07/GailForce-U.S.-Intelligence-community-confirms-ongoing-Russian-malign-influence-operations-at-Aspen-Security-Forum-480x384.jpg)

![Image GailForce to Space Force: 'Make it so' - the Space Force debate continues [Lima Charlie News]](https://limacharlienews.com/wp-content/uploads/2019/05/Space-Force-01-150x100.png)